[CVE-2021-34786] Cisco BroadWorks - Delete Admin Account
Hello Everyone! Today I will talk about my last findings at Cisco products BroadSoft BroadWorks, one of Cisco's products.
CVE-2021-34786: IDOR lead to delete arbitrary admin user accounts

Content
BroadWorks structure
At BroadWorks, we have an Admins group which have admins with write and read privileges and other admins with read-only privileges.
Read and Write: he can modify his data and other admins' data. Also, he can add users, change system preferences, delete users, and fully control the system
Read-only: he can modify his data and delete his account. He doesn’t have any other privileges “In my case”
I’ve got the second role (Read-only) and my task is trying to escalate my privileges to have Read and Write actions.
Exploitation
Following up with the previous CVE for the same application, you can check it here for your reference. I've tried to delete my account and intercept the request.
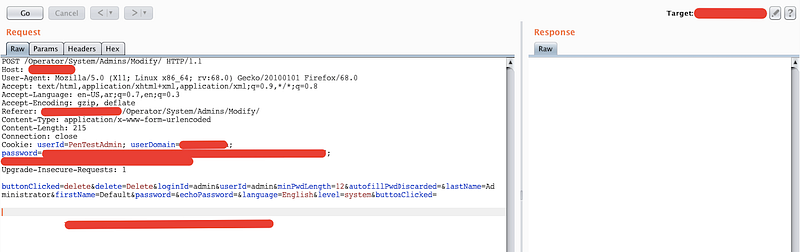
We have the same required parameters firstname/lastname/loginid and the same exploit, just replace them with Admin account data and send the request.
What are the results? The admin account was deleted 😈

Weakness points
At the change password function, it MUST ask me for the old password and if I forget it, it should ask me to contact the system administrator.
There’s no CSRF token attached with the user session to protect the system from performing the same attack using CSRF [I have tried it and successed]
To delete an account, it MUST ask the user to enter his password or any security question
Thanks for reading <3 Stay in touch
Last updated