Tabby Walkthrough
Hey folks, Here we come back again to continue HackTheBox machines series with “Tabby” machine, before we get started let’s take a look at the machine's info

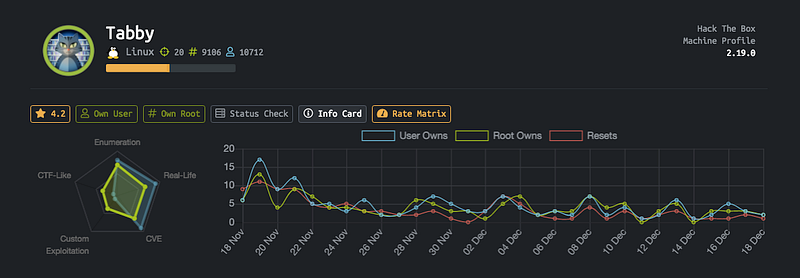
As you can see it’s easy but in my opinion, it should be medium because it has in every step something new and seems to be hard for beginners, let’s get started…
We will work on it without
Metasploit
As usual, we will begin our walkthrough with nmap scan to get all open ports and service running on them, let’s perform a standard scan
We have 22/80/8080 are open and services apache 2.4.41 / openssh 8.2p1 /apache tomcat so what we will do ?
Try to search for exploits in
apache 2.4.41by usingsearchsploittoolTry to brute-force
sshcredentials by usingnmap scriptsandbrutespraytoolTry to brute-force
tomcatcredentials by usingmetasploitandnmap scirptsTry to enumerate websites at
10.10.10.194:80and10.10.10.194:8080and content discovery by usingdirbuster/dirsearch/ffuf/gobuster
Let’s start…
Enumeration
We will try to enumerate the services to get the misconfigurations and vulnerabilities.
Public exploitation
I’ve searched for public exploitation in exploit-db and rapid-7 and public websites for exploitation for apache 2.4.41 / openssh 8.2p1 but unfortunately nothing we found
For Tomcat we found exploitation at rapid-7 and exploit-db but we must know tomcat credentials and the manager path, so we will need it later not now
SSH Credentials
I’ve brute-forced ssh credentials by using nmap and brutespray but nothing useful!!
Tomcat login credentials brute force
I’ve brute forced the credentials but also nothing useful, we used metasploit
Check the method at Metasploit
Website Enumeration and content discovery
At first I will open 10.10.10.194:80
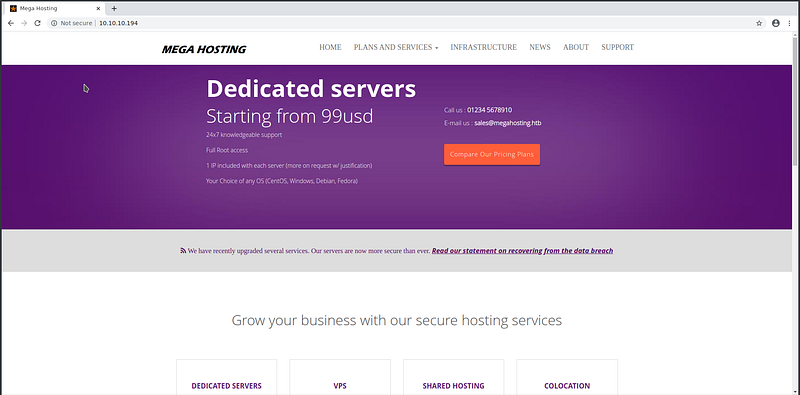
Nice, we have a website that seems like more websites in real life, and it seems like hosting websites so let’s discover it and check its source code
While checking the source code we found this link megahosting.htb/news.php?file=statement so we need to add this domain megahosting to the /etc/hosts by adding it like this line to the /etc/hosts file
10.10.10.194 megahosting and then we will access the upper link

let’s search for megahosting exploit as Google, it may be affected by custom exploitation.
We have found this one

Exploitation
Until now we don’t know our version, so let’s try this exploit in the upper link megahosting.htb/news.php?file=statement

Good, it’s vulnerable also.
Let’s try to get any information from tomcat directories, it may have sensitive information
After some enumeration, I’ve found a bunch of directories in these links
and also search for the tomcat-users.xml location file and found it in them, so let’s try to open all of them by using burp intruder or anything else

/var/share/tomcat9/etc/tomcat-users.xml is available and has credentials for the admin-gui and manager-script so let’s take these credentials and try to upload a reverse payload
Note: one of the privileges of admin-gui and manager-script is to deploy files on the server, so we will create a reverse payload and then deploy it
and then you can access it by open nc <port-number> and access the webpage megahosting:8080/shell

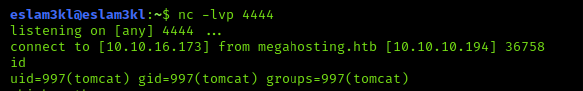
So for now we’re into the server but not in the user role, so let’s discover our privileges by opening the uses directories

We can’t open the user directory, so let’s try to get more privileges by searching for any important directories or files
After some enumeration, I found this backup file in /var/www/html/files

So I will try to download it on the local machine and look at its content
We will transfer it by opening a server on the vulnerable machine and accessing it from the attack machine
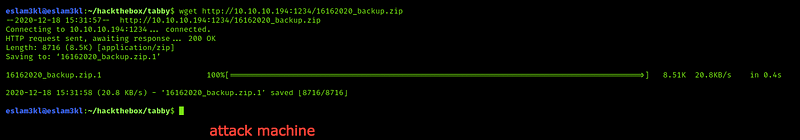
Now we have it on our attack machine, let’s try to unzip it by unzip file-name

It’s protected by a password, so you can use hashcat or john the wripper to crack the password, I’ll use fcrackzip because it doesn’t take much time
And we have the password admin@it
After trying to unzip the file I found nothing useful inside it so let’s use the password in other way
Let’s try to use it to login as ash user → su ash and insert this password

Good we have more privileges now but not the user privileges so let’s grab the user.txt first

Good, for now let’s try to find anything led us to the root access.
If you noticed the ash user is in lxd group

So after some google searching about how to use this role to be a root user, I’ve found an awesome resource to do it
Before we follow this resource let’s get first interactive shell because it will not work on the normal shell
It will get you in the interactive shell to be manage to access lxd then do as this man do exactly
As you will find in the upper link I’ve downloaded the tar file and transfer it to the vulnerable machine as you can see

After that, I compiled it on the victim machine and create an image

The final step is to access the image which we create


Let’s get our root.txt from the root directory

There’s nothing in this directory

It seems that he’s kidding me :)
Let’s search for the flag in all directories
After some search, I’ve found ❤

Last updated