CTF ringzer0ctf — SQLi challenges — part 1
All Right! Here we’ll deep into the most interesting vulnerability for me, it’s a SQL injection ❤
CTF ringzer0ctf — SQLi challenges — part 1
All Right! Here we’ll deep into the most interesting vulnerability for me, it’s a SQL injection ❤
Let’s solve some CTF challenges about this topic from ringzer0ctf website.

Challenge 1 — Most basic SQLi pattern.
From it’s name it seems that it’s the easiest way to solve sqli challenge, you will found a login form and the first try is to inject this payload
admin’ or 1=1 #

Good, it’s worked ! You have the flag and congrats to the first point ❤
Challenge 2 — Random Login Form
Here the situation is different little because you have two forms, the first one is login form and the second is registration form. If you tried to register an account with username:admin you will have a message that this account is already exist so try to login into it with our simple trick
username: admin & password: aykalam’ or 1=1#
but unfortunately you will get an error message, you failed to login with this trick and i tried more than trick but it doesn’t work

Now we don’t have any way from creating account with username admin.
After tried more and more and searching I've found something tricky, try to register an account with this credentials
username: — — admin — — &password=anything_you_want
Note: The — character is spaces.
By adding for example 4 spaces before and after the username it will pass the validation and will be deleted into the system or the database so you will bypass the validation and register with admin username, the password any word you want
Now try to login again

FLaaaaaaaaG :) Congratulation for the points ❤
Challenge 3 — Po po po po postgresql
If you logged into this challenge you’ll get a login page which by default you’ll use the simple technique by inject ‘ (comma) in the username filed to notice the balance the query in the backend, for example the backend balance the query bu inserting ‘ or “ or ‘) or “) or nothing, and so on.
By inserting ‘ you will get some thing nice, an error message which demonstrate the balancing query method, Nice :)

From the screenshot and the error the backend balancing the query by ending the query with ‘) characters so we’ll try to inject it with our payload, but wait and see the error again
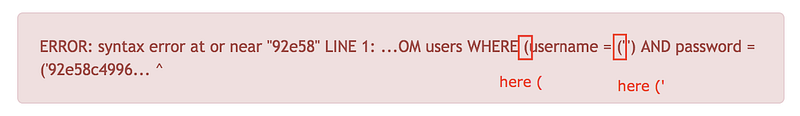
You’ll have inserting 2 ) because there’s one in the start which need to be closed so the balancing here is ‘)) not ‘)
username: admin’)) —
Good! We got it !
Challenge 4 — Login portal 1
After going into the challenge you will see another … what !! login page again !!

so let’s deal with it by the default payload ‘ and there’s no error messages appear !
try to inject this payload → admin ‘ or 1=1 # and you will see this message Illegal characters detected.
Nice, so the system has validated my input and have a black list to some charachters like # and =
so we will try to find alternative for this char
from this list WAF-GitHub. you will find more than technique to bypass filtered chars
you can use > or < instead of = in this way
username: admin’ or ‘a’>’b
trying this method…
We have 2 points NOW, Good !
Last updated