CTF CyberTalents — Admin Gate First
CTF CyberTalents — Admin Gate First
Welcome to the write-up of how to capture the flag of the challenge “Admin Gate First” from CyberTalents

Challenge info.
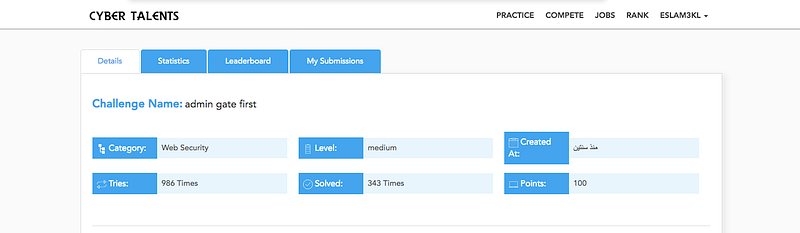
Challenge description: Flag is safe in the admin account info
From the description of the challenge you’ll notice that the flag is in something related to the account info like cookies for example
Lets start the challenge
When you entered to the challenge you’ll get login page with test user account credentials, check the source code but you’ll not find anything interested!
So let’s get logging into and see the source again

Check the source code
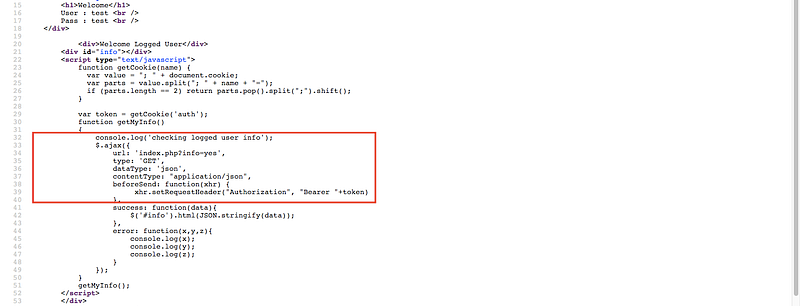
Note that there’s check of the authorization header so let’s relaod the page and check the request headers
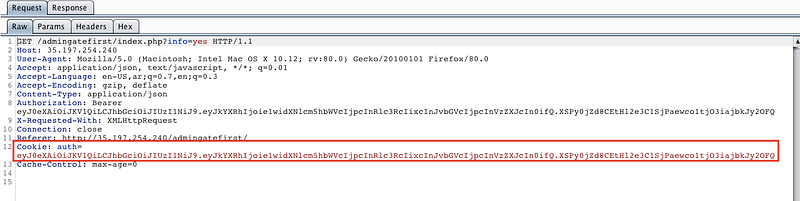
You should note that there’s JWT (JSON Web Token) which check the user role, so now we’ll note talk about it more but you should know that it consist of 3 parts Header, Payload and Signature and all of this parts are base64 encoded so the website jwt.io deals with this format and get it decrypted, so let’s go there and paste our jwt format in its place
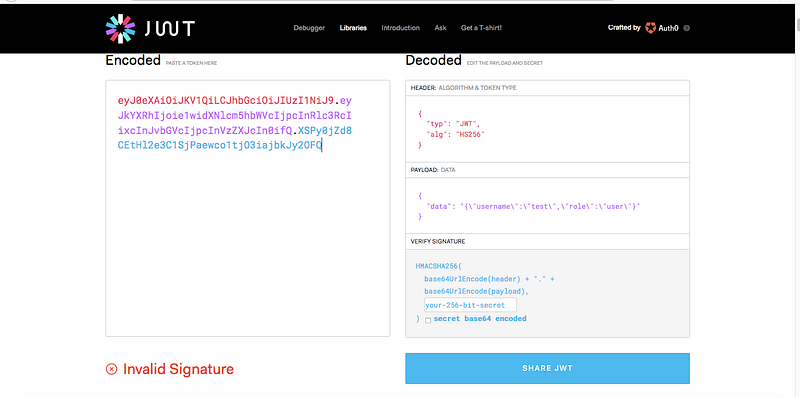
Before we continuing you should know about the 3 parts of the JWT so if you don’t know about the content of them read this first and continue https://jwt.io/introduction/
If you notice in the 3rd part Signature there’s our secret key can be edited, if you don’t know how dangerous of it or how this key is used for see this screenshot
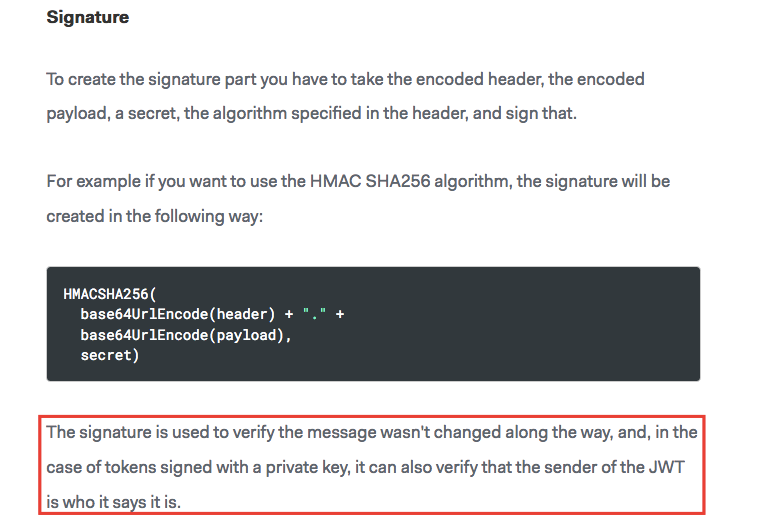
So in this case we’ll try to predict the value of this key. You can use a lot of tools which make the same thing but I prefer JWT-Cracker tool to do this mission
Download it from here https://github.com/lmammino/jwt-cracker
How to use it ?
token: the full HS256 JWT token string to crack
alphabet: the alphabet to use for the brute force (default: “abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789”)
maxLength: the max length of the string generated during the brute force (default: 12)
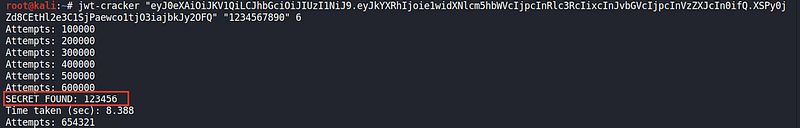
Note! our value is 123456
Go to jwt.io and put it into it’s place and change the username and the password to admin and copy the new JWT and replace it into the authorization header in the request
To know more about Bearer authentication https://swagger.io/docs/specification/authentication/bearer-authentication/
See What will happen !
Bingoooo! We’ve the FLAG :”)
Last updated