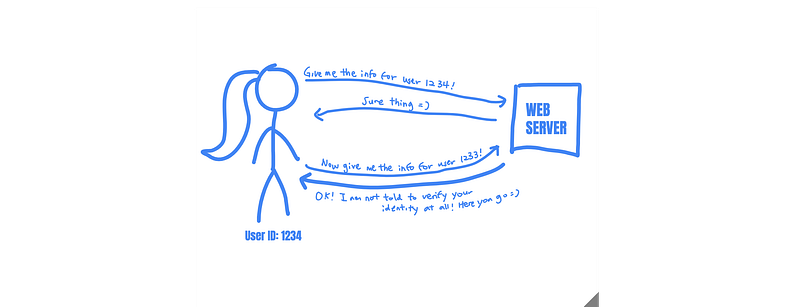
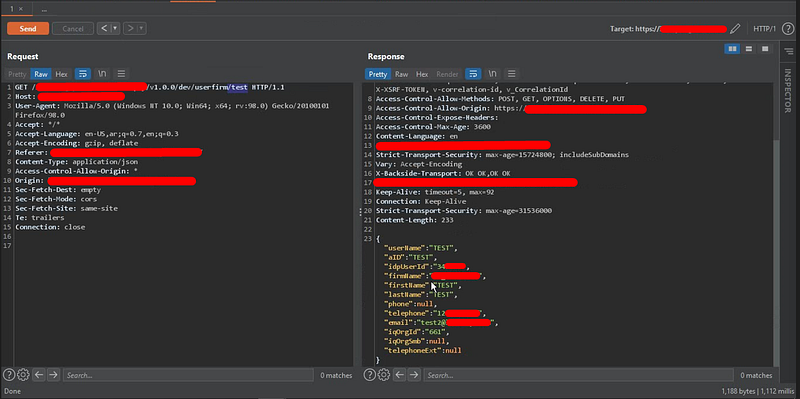
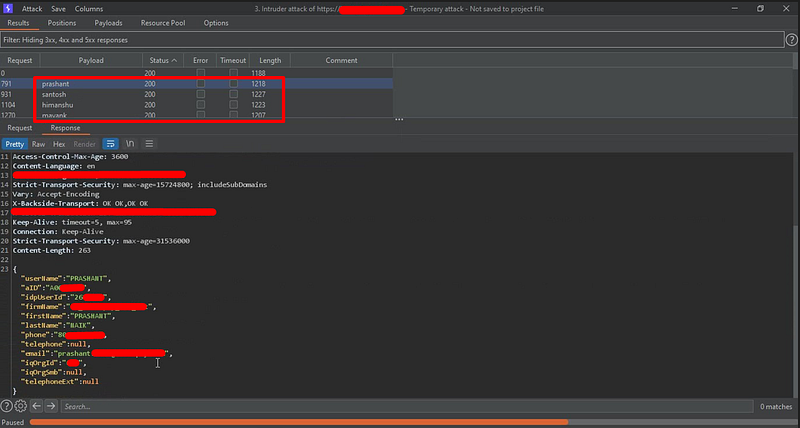
IDOR at Login function leads to leak user’s PII data
Vulnerable Login function leads to leaking PII data for all registered users.
PreviousAuthentication bypass using empty parameters.Next[CVE-2021–34785] Cisco BroadWorks - Privileged Escalation
Last updated